Old Defense Department Silos Must Be Swept Out
 |
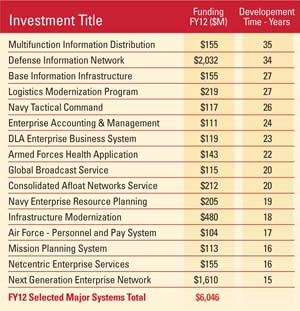
Silos have a long history in the U.S. Defense Department. They often stretch for decades. During a long development time, they create distinctive formats that keep reducing their interoperability with other solutions. The chart below of some long-term projects accounts for 18 percent of total IT spending.
Over time, any information technology investment will lock in unique codes and interface formats. Programs continually will be re-written to update technologies. Maintaining connections will require continuous modification of the supporting infrastructures of silos. Format translations and compatibility bridges for files will have to be constructed and maintained. That adds large amounts of support costs and increases the problems of maintaining security.
The Defense Department cannot afford the continuous stream of maintenance costs associated with decades-long software development cycles. As an immediate remedy, it is now in a position to acquire software that will accelerate the adoption of information-as-an-infrastructure (IaaS) solutions. Hundreds of cloud services firms now offer such technologies. They range from proprietary solutions to open-source solutions.
The Defense Department can start migrating to a much smaller number of infrastructures. This can be done by evolutionary migration. Each legacy silo application can be encapsulated into a virtual package so that it can run on its own virtual computer.
Such virtual computers can take advantage of pools of shared servers, disk memory and a shared communications environment. Capacity utilization then will increase, and security policies will be enforceable across an entire range of virtual computers. The conversion to IaaS services would become one of the principal means for delivering the projected reductions in the number of data centers.
 |
Instead of elongating project schedules for individual silos, the Defense Department in very short order should be able to evolve to a much smaller number of enterprise infrastructures, each subject to central controls for ensuring data and communications interoperability. Such migration could start in the next fiscal year by shifting processing of parts of some applications from legacy silos to a limited number of commercial public clouds from where they would support “hybrid cloud” solutions. After sufficient experience is gained, parts of such solutions could then relocate into Defense Department-owned and -operated private clouds.
The department will need to find a method for extracting funds from increasingly obsolete legacy programs to joint enterprise projects that offer a shared infrastructure. This type of move would allow Defense Department components to concentrate on applications, but without their prohibitively expensive custom-made infrastructures.
The original 1992 reason for creating the Defense Information Systems Agency was to make it a shared provider of enterprise services. The fiscal mechanism for delivering such services long has been available as working capital funds that can be used to charge individual users—not as allocations of fixed costs, but as a fee for services used. Transaction-based pricing will have to be instituted in this new environment so that components can make competitive comparisons as they shifts cloud workloads between cloud services in a hybrid environment.
Paul A. Strassmann is the distinguished professor of information sciences at George Mason University. The views expressed are his own and not necessarily those of SIGNAL Magazine.
SIGNAL Online
We welcome your comments on this column at http://bit.ly/insignal1011-01, or e-mail us at signalnews@afcea.org.




Comment
Professor Strassmann has
Comments