Moving Beyond Traditional Risk Labels: Redefining Patch Management
Third-Place Winner in 2025 The Cyber Edge Writing Award.
In recent cyber activities that have exposed alarming vulnerabilities in U.S. critical infrastructure, cyber criminals demonstrate the ability to disrupt vital services, like energy, water and transportation. Cyber-criminal techniques and methods underscore the urgent need for a more resilient cybersecurity strategy. Among the necessary shifts, patch management stands out as a critical area in which outdated approaches fail to adequately protect U.S. high-stakes infrastructure.
Historically, patching has relied on labels like “critical,” “high,” “medium,” and “low” to determine the urgency of a security fix. However, in sectors where even minor disruptions can lead to severe consequences, these labels often create a one-size-fits-all approach that neglects the unique priorities of business function. The birth of a new model is needed, one focused on business-driven definitions of risk, that could improve the security and resilience of critical infrastructure. By aligning patch priorities with specific business impacts, organizations can focus resources where they’re needed most, ensuring that the right systems receive timely protection against cyber criminals.
The Threat: Static Risk Label Leave Infrastructure Vulnerable
Cyber attacks against critical U.S. infrastructure are evolving, and the recent activity from various groups demonstrates that hostile nation-states are increasingly targeting these vital systems. In many cases, these attacks aim to cripple or disrupt services, impacting the daily lives and safety of millions. Cyber criminals’ tactics focus on exploiting vulnerabilities in infrastructure networks that are slow to adapt to emerging threats. Attackers use these entry points to establish persistent access, positioning themselves to launch a disabling attack. In response to attacks, many organizations deploy patches based on severity levels. “Critical” and “high” vulnerabilities typically prompt immediate action, while “medium” and “low” risks may be deferred.
These labels often overlook operational context. For instance, a “medium” vulnerability on a water treatment system with open internet access could carry more risk than a “critical” vulnerability on an isolated human resources system. In critical infrastructure, a delay due to improper prioritization of patching can have far-reaching consequences, from public health risks to economic disruptions. As cyber criminals advance, capitalizing on patching delays and targeting under-prioritized systems to gain access is an advantage.
A Solution: Business-Centric Patch Management
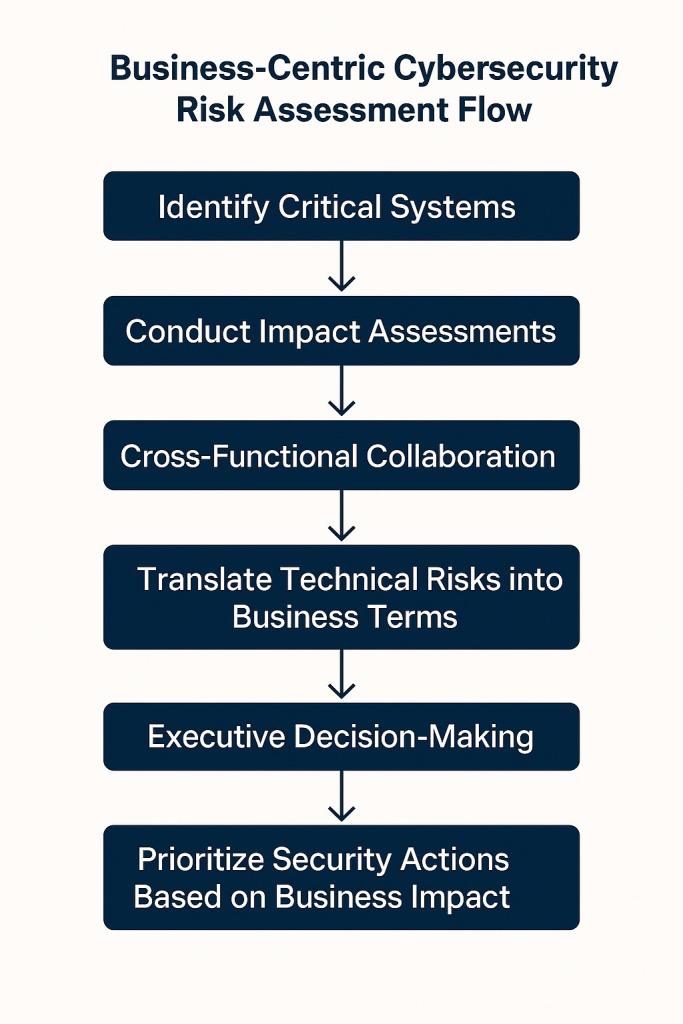
A shift to a business-driven approach in patch management would allow cybersecurity teams to move beyond labels and evaluate vulnerabilities based on the unique needs of each infrastructure. This approach acknowledges that not all “critical” patches are of equal importance and that business impact should dictate prioritization. By understanding the specific services each system supports and whether sensitive information is present and displaying potential consequences of exploitation, organizations can apply patches to systems that truly require them first. Implementing business-centric patch management would involve several key steps.
First, organizations would conduct impact assessments to determine the criticality of systems based on their role in essential functions, like patient care in hospitals or grid stability in power utilities. Second, these assessments would involve close collaboration between cybersecurity teams, system administrators and business leaders. This approach would provide a dialogue where information technology (IT) teams can translate technical risk into business terms, allowing executives to make informed decisions that align security efforts with organizational priorities. For instance, consider a power grid operator facing a newly discovered vulnerability in its control systems. Under traditional labeling, this vulnerability might only receive a “medium” risk classification based on technical criteria, leading to delayed patching. However, a business-centric approach would highlight the vulnerability’s impact on service continuity, prompting action to prevent potential power outages and minimize safety risks.
Ongoing and Necessary Steps for Implementation
Shifting to business-centric patch management requires a combination of items such as policy updates, training and improved communication. Many organizations are exploring similar models, particularly in sectors that have high compliance requirements and or operational risks. To fully adopt this approach, organizations need a clear framework for translating business impact into actionable risk prioritization. It could include integrating business-centered risk metrics into existing patch management tools or developing cross-functional task forces to assess vulnerability impacts. One such example of a proactive adaptation is within the energy sector, where the Department of Energy has collaborated with private utility companies to share intelligence on potential vulnerabilities that might disrupt the national power grid. Such partnerships could extend to other infrastructure sectors, supported by agencies like the Cybersecurity and Infrastructure Security Agency (CISA), which has advocated for critical infrastructure owners to shift to more adaptive strategies. Training programs for cybersecurity professionals should address the skills needed to communicate business impact effectively. Business leaders and IT teams would benefit from cross-functional workshops that break down technical risks and align both teams around core business functions. By obtaining a mutual comprehension of business-critical functions, these programs help prepare teams for quick, coordinated responses to threats of any kind.
Challenges and Recommendations for Overcoming Obstacles
Transitioning to business-centric patch management is a significant change for the industry and may encounter resistance, particularly from teams accustomed to technical severity labels. Cybersecurity teams often face limited staffing and tight budgets, making it challenging to invest time in new assessments. To address these barriers, organizations can take several practical steps:
1. Gradual Implementation: Rather than an organization-wide rollout, a business-centric model can be piloted within select departments. This approach allows organizations to refine processes before expanding them and provides early success stories for the broader transition.
2. Executive Support: C-suite backing is crucial to legitimizing the shift away from traditional risk labels. Executives should champion the approach by setting organization goals that prioritize cybersecurity aligned with business functions, ensuring that resources are directed to attributed areas.
3. Public-Private Partnerships: Collaboration with government agencies and industry organizations can provide resources and intelligence needed to assess the business impact of vulnerabilities. Agencies like CISA and the National Institute of Standards and Technology offer guidelines and frameworks for sector-specific risk assessments that can guide patch prioritization.
4. Enhanced Training and Certifications: To support this shift, cybersecurity and IT teams should pursue training programs that emphasize business communication skills, enabling technical experts to frame risks in ways business leaders can understand. Certifications that focus on integrating business objectives with cybersecurity practices could also help bridge the gap. By addressing these challenges, critical infrastructure sectors can implement business-centric patch management without overwhelming cybersecurity resources.
Building Resilient Critical Infrastructure
The evolving threat landscape demands that critical infrastructure sectors adopt a more resilient, adaptive approach to cybersecurity. As seen in recent actions, attackers are exploiting legacy vulnerabilities and targeting systems based on their impact on essential services. In this high-stakes environment, traditional risk labels are no longer sufficient. A business-centric patch management model redefines risk by aligning patch priorities with business impacts, ultimately creating a more proactive cyber defense for critical infrastructure. By encouraging collaboration, securing executive support and fostering public-private partnerships, organizations can overcome the challenges of implementation. In the face of sophisticated cyber adversaries, critical infrastructure operators must focus not just on which patches are “critical” in a technical sense but on which vulnerabilities pose the greatest risk to their business operations. By shifting from severity labels to business-driven definitions, the cybersecurity industry can enhance the resilience of our nations and most essential systems and better prepare for the threats of tomorrow.
Matthew Maynard is a cybersecurity researcher with more than 18 years of experience in IT and InfoSec. He currently serves as an incident response analyst III and Purple Team lead at BJC HealthCare, focusing on proactive threat hunting, adversary emulation and improving cyber defenses in the health care sector. He also investigates dark web forums and cyber criminal ecosystems, providing insights into threat actor TTPs, stolen data life cycles and emerging attack trends





Comments