Silence on Cyber Crimes Endangers Critical Infrastructure
Second-Place Winner in 2025 The Cyber Edge Writing Award.
Improving trust in the cyber crime reporting process is paramount to the cyber defense of our nation’s critical infrastructure, as it allows law enforcement to disrupt and capture the criminal groups responsible for the attacks. By engaging in simple policy and procedure changes, law enforcement agencies can remove doubts about the victim’s privacy when reporting and encourage future victims to come forward at a minimal cost.
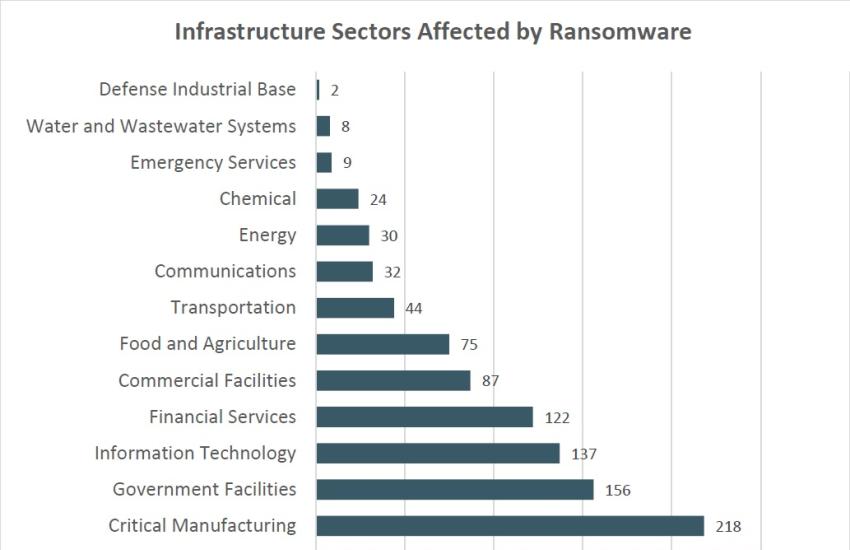
In their annual report published in April 2024, the Internet Crime Complaint Center (IC3) found that 14 of the 16 critical infrastructure sectors were affected by ransomware. Each of these sectors is considered so vital that their incapacitation could cause debilitating ripples throughout the economy, national public health and safety, and the security of our nation. In this same report, the IC3 estimates that crimes of this nature could be even more prevalent than what is currently known due to businesses underreporting crimes to enforcement agencies. The underreporting of cybersecurity crimes is not surprising, as public disclosure of these attacks damages the victimized company’s brand image to the public, directly affecting its bottom line.
Businesses typically communicate successes and failures in terms of profit and loss rather than vulnerabilities mitigated. In 2023, the IC3 reported $12.5 billion in losses due to cyber crime—a statistic with the weight to demand the attention of anyone involved. In addition to the findings from the IC3, a study was conducted by Comparitech, a cybersecurity research company, and found that publicly traded companies affected by a cybersecurity breach had stock prices that underperformed in stock market expectations by -3.2% on average for six months following a breach disclosure. To put that into perspective, the Change Healthcare breach is projected to have cost between $2.3 and $2.45 billion combined in upfront costs and lost stock gains. This does not include other secondary effects, such as the impacts of the Health Insurance Portability and Accountability Act (HIPAA) violations. According to the study, health care companies had the most severe impacts, while also having the highest number of reported ransomware incidents to the IC3 among critical infrastructure sectors. These companies have significant financial motivation to keep any cyber attacks under wraps. Unfortunately, this is counter to their interests and the benefit of others in their industry, as these reports contribute to the disruption of the criminals executing such attacks.
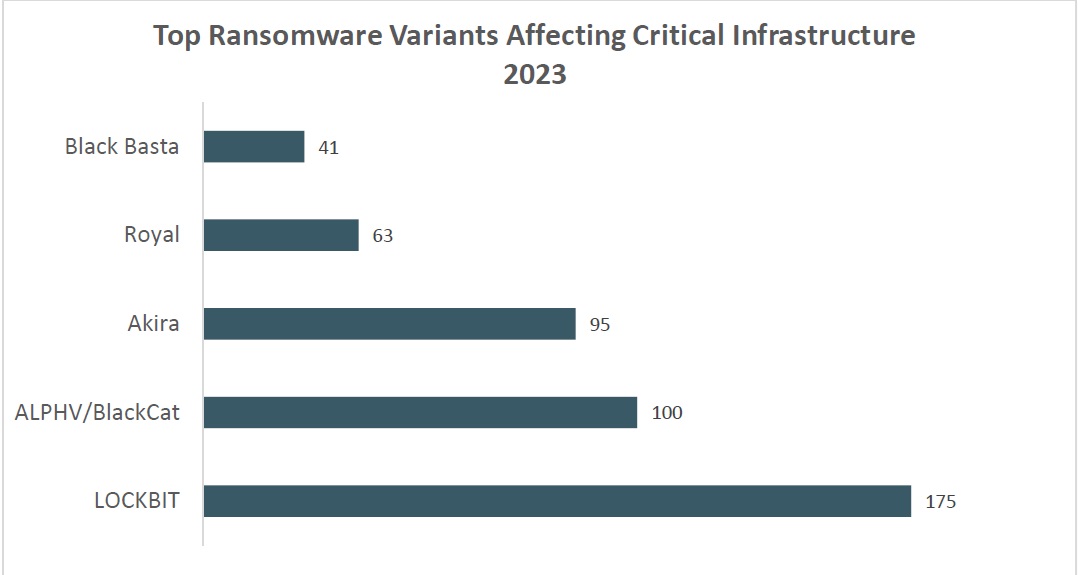
One of the challenges beyond getting cyber-attack victims to participate in reporting, in many cases, is that these criminals are located abroad. By abusing the global reach of cyberspace, they can commit crimes in countries that do not have extradition agreements or that do not criminalize cyber attacks as harshly. While global cooperation in the pursuit of criminals is the ideal, it may not always be a reality. In cases where we do not have the cooperation of the nation where they reside, we should continue to make every effort to impact their ability to operate. Then, by following up and publicly demonstrating that inhibiting Cybercrime-as-a-Service groups benefits both the United States and the nations in which the criminals reside, negotiations on further cooperation can be encouraged. The United Nations adopted a treaty toward this goal of international cooperation against cyber crime in late December. This convention is the first international criminal justice treaty negotiated in more than 20 years and provides the means to fortify international efforts to protect the public online. This kind of international cooperative effort to improve proactive preventative action against cyber crime is vital to protecting our critical infrastructure. One such example of these proactive efforts came earlier this year when the FBI seized the website of Lockbit, a Russian-based Cybercrime-as-a-Service group, no doubt in part due to information gathered from the incident reports of its victims. Part of that seizure included the keys needed to decrypt the information of ransomware victims, meaning those who reported through official channels may have had the opportunity to recover their operations. This group was by far the highest reported executor of ransomware attacks according to the IC3 annual report, making this a significant victory.
While this victory shows the efficacy of the information gained from reporting, those processes need to be improved to elicit greater trust from victims that their interests will be preserved, while still forwarding efforts to track down perpetrators. This is a vital effort so fewer of these crimes go unreported, and successes of this magnitude will continue. The current privacy agreement in the IC3 complaint form states how the substantial amount of information that is requested may be used, but offers no reassurances in terms of the privacy of the identity of the victim. The amount of identifying information that is collected, combined with the absence of a guarantee of privacy, serves to dissuade victims from reporting due to the significant financial and reputation risks. To provide freedom from doubts surrounding the risk of public disclosures as a result of reporting, agencies should include language in their privacy agreements that provides specific assurances their information will not be released to a wide audience in a way that identifies them as having been a victim. While some personal information can be omitted from the form provided by the IC3, further efforts should be made to provide more anonymity for the reporting company while maintaining the required information to proceed with the investigation. For example, more anonymous forms of communication could be prioritized, such as email, instead of requiring phone numbers and full addresses. This layer of anonymity will encourage more potential reporters to come forward, increasing the information available to law enforcement and ultimately providing for the defense of our infrastructure sectors on the cyber front. At the same time, this will allow private companies more control over how these breaches are reported to the public so that their trust is maintained, rather than unintentional reporting by a third party before damage control has happened.
Encouraging participation further could also be done through the way that press releases are conducted. Including the number of reports that assisted in the seizure of cyber criminals’ assets or their capture, and praising the victims’ contribution without revealing their identity, would provide welcome positive feedback. Communicating wins in the context of losses prevented would also provide a greater understanding of their impact on the business community. This kind of public praise will encourage infrastructure members and their peers to offer tips or report incidents by setting an example that they do not have to fear the potential consequences of reporting and that their efforts make an impact. This foundation of positive reinforcement will help to build a culture that sees cybersecurity less as a necessary evil and more as a contribution to justice that helps everyone involved. These efforts have the advantage of being simply policy and procedure updates, meaning there isn’t a need to wait for new technologies or research to come to fruition. The monetary cost to implement this plan would also be low since there is no need for additional personnel or equipment for these suggestions to work.
Choosing between reporting a ransomware attack to law enforcement and hiding the truth to protect the bottom line should never be a consideration for a business. It is imperative that we tip the scales so that the benefits of reporting outweigh the costs. Improving the public perception of reporting, combined with allowing businesses to better protect their image when reporting through a greater level of anonymity, will increase the rate at which these crimes are reported. This will ultimately give law enforcement the tools they need to prevent these attacks before they happen, thereby preventing cyber attacks that threaten our national security.
Staff Sgt. Logan Houston has served five years active duty in the U.S. Air Force. He is currently assigned to DISA, and has also written for Crosstalk: The Defense Software Engineering Journal. Houston holds an associate degree in information systems and is currently pursuing his bachelor’s degree in software engineering.
Graph from IC3 April 2024 annual report.




Comments