Telephony Convergence Poses Security Risks
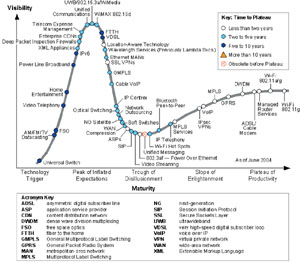 |
| Expectations for new capabilities tend to peak soon after a need is identified then fall significantly as soon as the challenges are identified. |
Integration of new and legacy communications technologies demands safeguards.
The convergence of telephone and Internet protocol networks holds great promise, according to industry experts, leading vendors and the press. However, an increasingly converged network also increases the risk factor associated with securing voice and other real-time communication streams. These risks are not limited to Internet-protocol-based networks; traditional time division multiplexing networks also are vulnerable.
Threats to the U.S. national communications infrastructure range from very limited attacks by script kiddies to industrial espionage to cyberterrorism and information warfare. The concepts behind cyberterrorism and information warfare have been around for some time. Hackers, crackers and virus writers have been maliciously attacking the Internet and, to a lesser extent, the public switched telephone network for decades. The tools, methodologies and technologies used by those with malicious intent are well proven and are the underlying fundamentals of cyberattacks.
As converged voice service technology is deployed, legacy technology will continue to be used in large scale. This migration period will spawn very large, complex hybrid networks that will be far more vulnerable than either pure legacy time division multiplexing (TDM) or pure Internet protocol (IP) networks. While cyberattacks against voice and related real-time communication services are relatively minimal today, as communication networks converge, incidents are likely to increase, and future cyberattacks could be launched by a terrorist organization as part of a larger military campaign or a cyberwar.
The assumption has been that the focus of cyberwarfare would be the disruption or extended exploitation of data networks and associated systems. According to Jeff Pulver, chief executive officer, pulver.com, the increasing pace of deployment of convergence technologies demands that voice systems, both old and new, receive the same amount of attention for security as data networks have in the past.
Communications vulnerabilities exist in both traditional TDM networks and convergence networks. While industry hype focuses on convergence communications, legacy communications security also is critical. TDM voice will remain a highly volatile and dynamic hybrid environment comprising multivendor products of both legacy TDM technology and newer convergence technologies.
Convergence communications are nonsecure primarily because of the timing and allocation of engineering resources. They have is become truly deployable only in the past 18 months. Prior to that, engineering resources were focused on maturing real-time communications, voice over Internet protocol (VoIP) technologies and products to a deployable level of maturity. This was necessary even if it left products less secure than desired. However, VoIP is just one of many technologies needed to support the wide-scale use of real-time communications across local and wide area networks. Other necessary technologies include multiprotocol label switching and session initiation protocol.
Understanding the security implications of the coming convergence revolution requires a better understanding of both the fundamental issues associated with legacy voice services and those associated with the newer convergence technologies. Traditional voice networks and communications equipment are based on proprietary switching technologies and TDM-based network architectures. Traditional toll fraud operations against these legacy environments have steadily increased over the past few decades, and the pace is quickening. Interconnectivity between legacy voice networks and data networks via authorized and unauthorized modems remains a major, widely recognized vulnerability for data network security that has traditionally been difficult to manage.
Convergence networks, defined as packet-based networks transporting real-time communications streams, are susceptible to both traditional Internet protocol (IP) threats—including worms, viruses and hacking—and real-time communications-technology-specific threats. The latter includes a number of different types of attacks such as exploiting protocol vulnerabilities, both known protocol-generic and vendor-implementation-specific vulnerabilities. It also includes registration hijacking or impersonating a communications server to facilitate illegitimate rerouting of calls, to allow eavesdropping or to change requested communications security characteristics. The threats also consist of tampering with message bodies such as encryption session keys and malicious session modification. Finally, denial of service or “brute force” attacks could disrupt real-time communications, causing delay, jitter, packet loss or signaling disruption.
The past 10 years have seen significant progress in the capabilities of IP networks and the maturity of VoIP. In the past 24 months, large organizations and most service providers have started to adopt real-time communications and VoIP. For example, the U.S. Defense Department’s network-centric warfare initiative, an embodiment of information age technologies, will rely heavily on the Global Information Grid (GIG). This upgrade of defense infrastructure with leading-edge technologies includes an all IP-based network and in many ways mirrors what the commercial sector is doing.
The GIG is organized into classified and unclassified segments traversing undersea, land, air and space pathways. While the classified segments are highly protected secure domains, the unclassified segments interact with public communication networks to route communications to third parties. Because of this external connection, the unclassified segments are as vulnerable to all TDM and real-time communications threats as the commercial sector.
Legacy security techniques focus mostly on securing legacy voice networks and converged data/voice networks via cross-network connectivity, including modem and supervisory control and data acquisition implementations. This is accomplished via an emerging trend of enterprise TDM firewalls that monitor and control incoming and outgoing data communications over TDM connections.
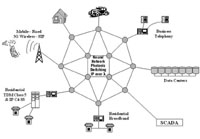 |
| As a network starts to include additional devices, each entry point becomes a possible point of vulnerability. |
Beyond the real-time communications security protocols, the implementation of devices that can perform deep packet inspection and protocol analysis is necessary. The protocol analysis is beneficial from both a security perspective and a protocol format perspective. Because of the immaturity of session initiation protocol devices, many messages are improperly formed by today’s equipment.
Ideally, in a converged world, both the real-time communications payload and signaling streams would be fully encrypted on the local area network, wide area network and Internet. Encryption provides the most secure way to send and receive VoIP and addresses the requirements of authentication, integrity and privacy. However, because of protocol and network architecture issues, this is not possible.
Encryption can be used effectively only if all devices across a network call-flow support it. However, despite vendor promises, a number of practical issues may prevent encryption from being widely used. For example, encryption is available for e-mail and other services but is rarely used because it is cumbersome.
Another issue is that the key value of encryption is its use for authentication of devices. It allows an IP private branch exchange to be sure it is talking to another IP private branch exchange telephone and prevents rogue devices from hijacking sessions, impersonating devices or initiating denial of service attacks. This model breaks down if even one nonauthenticated device is allowed to participate.
The third problem is that encryption totally disables the network address translation essential for real-time communications on network edges. For this translation to work, signaling must be decrypted and re-encrypted.
Finally, depending on what form is used, encryption makes signaling and media opaque to third-party security and management systems. As a result, if a signal is encrypted and a network problem occurs, it may be impossible to use a third-party system for diagnosis.
While encryption is key, it is not the only real-time communications security technique. Other techniques use encryption in different ways to provide authentication, integrity and privacy. These techniques draw on the open-systems interconnection-layered model concept in which a higher layer relies on lower layers to perform a given function.
Probably the most important and most difficult components of securing voice communications are establishing robust policies and procedures and implementing best practices, says Lee Sutterfield, chief executive officer, SecureLogix. Often when new technologies are adopted, policies and procedures lag behind, he points out.
Equally critical is the adoption of new policies and procedures by all organizational members. To fully benefit from the technology, enterprises need to issue overarching policy guidance that covers at least the need for voice network security, standards and guidance on voice security, the role of designated voice security managers, and training on voice network security.
Securing voice communications is not just an information technology issue. At the top, policies and procedures must be implemented and prioritized by senior leadership. At the worker level, individuals must follow policies and procedures because failing to do so creates inherent vulnerabilities. Finally, information technology organizations must design, implement and deliver secure networks.
David L. Fraley Jr. is a U.S. Army Reserve signal officer and a director with Gartner Incorporated’s federal practice, McLean, Virginia.
Web Resources
National Institute of Standardsand Technology Computer Security Resource Center: http://csrc.nist.gov
INFOSYSSEC: www.infosyssec.net/index.html




Comments