Enabling Cybersecurity in Space With Digital Engineering
Digital engineering and cybersecurity research have traditionally been treated as completely disparate domains. These two practices emerged from different areas of the technical universe, with different lexicons and technical characteristics. Bridging the two practices significantly improves and accelerates the identification and remediation of vulnerabilities in cyber-physical systems, including space systems. Bringing them together will decrease costs, improve development speed and enhance the security of vital space assets throughout their life cycle, from production and launch through on-orbit operations.
A few questions must be considered collectively as an industry to ensure success in the future:
Is a simulated environment sufficient for cybersecurity research purposes?
How can simulated environments and digital twins augment traditional vulnerability research and reverse engineering (VR/RE) practices?
Can data produced in this environment be used to train artificial intelligence/machine learning models to support cybersecurity research objectives?
From these questions, there are five identifiable key considerations for using digital engineering for cybersecurity research. These insights suggest future improvements to further strengthen digital engineering’s role in VR/RE.
The importance of digital engineering and the role of cybersecurity research
Digital engineering integrates modeling and simulation (M&S) into the product development life cycle. For products where development and testing involve unusual situations such as extreme operational environments, expensive hardware components or highly complex scenarios, digital engineering is a proven risk-reduction practice. Born out of the need to improve efficiency and performance, digital engineering can transform the way industries design, develop and maintain new products and capabilities.
The term “digital engineering” is often misunderstood, lacks an industry-wide adopted definition and can be ineffectively implemented. To overcome these obstacles, the following foundational principles of a sound digital engineering approach must be observed:
Single Source of Truth—When modeling a complex system with many subsystems (sometimes referred to as nodes or instances), the ability to share current and propagated state data across nodes ensures the system simulation is operating within a single source of truth. This means the system model and resulting simulation are inherently more robust and reliable.
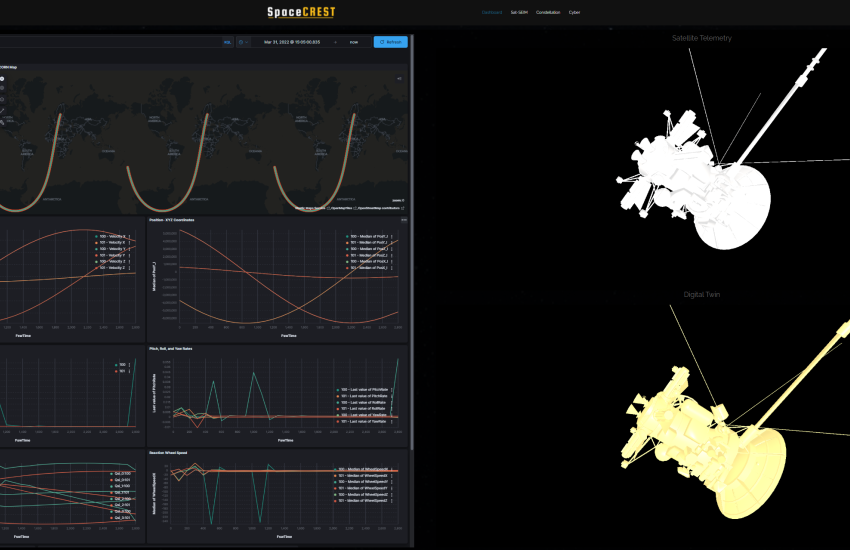
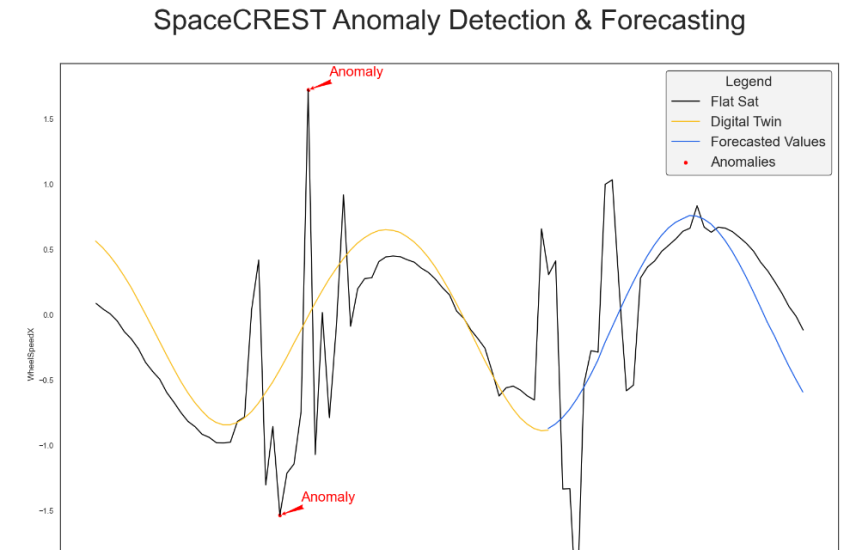
Digital Twin Artifacts—Engineers often iteratively add fidelity to models throughout their life cycle, which, when engineered properly, can be easily converted to digital twins of the operational system. The digital twins serve many different purposes, including anomaly detection and resolution, design updates and overall block design upgrades.
These principles create a common standard of digital engineering excellence and reliability.
Cybersecurity vulnerability research and reverse engineering is the practice of identifying weaknesses in electronic hardware, firmware and software using code analysis techniques. Reverse engineering seeks to understand how a system or application functions by decomposing it into component parts and then reconstituting how each part works together to perform the object’s intended function. A VR/RE researcher uses a variety of tools and methods, including physical characterization procedures (for hardware/firmware), code extraction and static and dynamic code analysis.

VR/RE is used to strengthen systems against exploitation through remediation of weaknesses or other mitigations. VR/RE traditionally relies on manual processes augmented with code analysis tools. Despite the highly technical nature of code, it is a specialized field that rewards tedious data review, scrupulous documentation, intellectual curiosity and hard-earned intuition.
With the explosion in the space economy and the push by the Department of Defense and Space Force to embrace DE, leveraging the advantages of the digital environment to improve cybersecurity offers great benefits to the space sector, defense industry and national security overall.
Five key issues to consider:
1. Model extensibility. While a single “good” model or simulation can be beneficial, the ability to add, remove and refine elements as necessary to achieve research objectives is even better. An extensible framework that allows models, components, systems and third-party tool integration, turns digital engineering into a veritable Swiss Army knife.
An advanced programming interface (API)-driven approach to the modeling environment, coupled with hardware-in-the-loop and software-in-the-loop capabilities, creates flexibility in the digital engineering environment. It also gives the ability to create “good-enough” elements and match them with high-fidelity model elements to create a heterogeneous modeling environment supporting system-wide impact assessments. Advanced APIs enable quick integration of any hardware component or software application. They provide a configurable abstraction layer that allows for efficient integration of subsystems, systems and/or entire segments with little to no impact on the rest of the architecture.
An open system architecture gives researchers more options for evaluating attack effects. As an example, one research scenario might assess the impact of a denial-of-service attack against a simulated reaction wheel on other components of the simulated spacecraft.
Researchers can create a “software-in-the-loop” camera module that reacts to the denial-of-service attack by pointing to a different spot on the Earth. An open systems architecture gives researchers more options to assess attack effects. This functionality also enables external research teams to bring their ideas or research objectives for collaboration within the same environment.
2. Enable the M&S System. Without the ability to monitor, interact with, operate and maintain the digital environment, it can become an unwieldy, suboptimized ecosystem. Properly wrapping the M&S system in a well-provisioned and tooled infrastructure produces more valuable insights.
The infrastructure should include robust data capture, storage, analytics and visualization capabilities to fully support interactive tooling and data analysis. Several full-stack options can provide this infrastructure. One is a Nutanix compute cluster running Elastic’s ELK stack to support these functions and augment the M&S system’s native user interface.
The compute cluster should support digital twinning through cloning of the simulation under test, which enables the creation of parallel running simulations. This also supports replay and Monte Carlo methods and captures data to support statistical analysis and model training for artificial intelligence/machine learning research.
3. VR/RE outcomes correlate directly to model fidelity. While not every simulated system requires a perfect model, as complexity increases, so does the inevitability of unexpected interactions between systems. To provide meaningful results, the fidelity of the simulation must be thoughtfully designed to ensure reasonable accuracy, and model deficiencies must be considered and improved when necessary.
In the world of M&S, not all simulations are created equal. Physics models emulate the characteristics of a system, and systems relationship models (such as model-based systems engineering software) mimic the relationships between systems but do not necessarily replicate the protocol-level behaviors of the system. In a mixed space simulation environment, one component may emulate the physics of a spacecraft element, another may be an actual hardware element in the loop and all of it may be connected to a virtualized ground segment.
Therefore, understanding the limitations of the environment is extremely important. To establish full protocol-level packet traceability throughout the system, all elements must be high-fidelity protocol level emulations to answer specific vulnerability questions. As a library of high-fidelity emulated components is developed, the depth of possible vulnerability research increases over time. Even with these limitations, the ability to automate attack scenarios and assess physical effect propagation throughout the spacecraft is invaluable.
4. Fundamental vulnerability research principles apply. Traditional vulnerability research principles are enhanced, not replaced. The integration of digital engineering does not invalidate the tried-and-true tools and techniques of the industry; rather, it enables innovative ways to apply those tools to provide more meaningful and efficient value.
A vulnerability assessment framework should leverage traditional VR/RE methods within the digital engineering environment. These methods should be familiar to most VR/RE professionals: static and dynamic analysis using existing best-in-class tools like IDA Pro, Ghidra and others. One focus of the digital engineering element of the framework is the addition of behavioral analysis through simulation. This supports the ability to rapidly create, script, automate and monitor scenarios and enables data normalization methods to support statistical and machine learning comparison and analysis of each simulation run.
5. Don’t forget about reality. Real-world data validation builds confidence in findings and decisions based on digital engineering approaches. It is essential to check against digital models to ensure that the simulation environment matches the operational environment. This is especially true when developing rules based on machine learning analysis of synthetic data produced by the M&S system. For synthetic data used to develop anomaly detection models capable of providing indications and warnings of an attack against a spacecraft, the model and the data must be validated by comparing them to real-world baseline data. This validation process also creates a feedback loop for model refinement, further enhancing the utility and accuracy of synthetic data.
Digital engineering promises a bright future for cybersecurity research
Not only is it possible to use digital engineering platforms for cybersecurity research, but it’s cost-effective, and the quality of the research is on par with an evaluation of an actual cyber-physical system. This conclusion comes with important caveats, as identified earlier, but as the two disciplines continue to evolve, the efficacy of employing digital environments for VR/RE purposes will only increase. Continued integration of the two disciplines is certain to lead to more secure space systems.
Brian Pate leads the Cyber Operations Business Unit at BigBear.AI, focusing on full-spectrum cyberspace services and solutions support to U.S. Cyberspace Command, service cyber components, Department of Homeland Security Cybersecurity and Infrastructure Security Agency, and other U.S. government organizations with cyberspace missions. Additional contributors to this article include Joe Davis and Steven Durr, principal vulnerability researchers at BigBear.AI, and Alex Dunn and Danielle Cleveland, mission architects at Redwire Space.
The opinions expressed in this article are not to be construed as official or reflecting the views of AFCEA International.






Comments