Microelectronics Offer Case Study for Securing Defense-Critical Supply Chains
Emerging cybersecurity technology innovations can and must support the design of more secure, resilient and efficient defense-critical supply chains, including microelectronics essential to national security and economic prosperity.
U.S. critical supply chains are under siege. State-sponsored cyber actors are enlarging their threat vectors in both capabilities and active intentional use in supply chains. China’s laws and policies support the active use of human intelligence to gather information regarding supply chains. Recently, Chinese advanced persistent threat (APT) supply chain attacks were used to steal data from companies and their customers. These attacks were initiated by APT41 (also known as Barium, Winnti, Wicked Panda and Wicked Spider).
Russian state-sponsored cyber actors also have demonstrated capabilities to compromise information technology (IT) networks by using mechanisms to maintain long-term, persistent access. This access allows exfiltration of sensitive data from IT networks—and also operational technology networks—by deploying destructive malware to disrupt critical industrial control systems and operational technology functions.
Russia also actively targets critical energy infrastructure. Berserk Bear (also known as Crouching Yeti, Dragonfly, Energetic Bear and Temp.Isotope) targeted entities in Western Europe and North America, including the energy sector industrial base, transportation systems and defense industrial base sector organizations.
Additionally, the volume of cyber vulnerabilities in U.S. systems continues to increase dramatically. Adversaries now have greater freedom and political support within their home countries, and financial support from adversarial governments to deliberately introduce vulnerabilities into critical infrastructure in the United States and other countries. The “Triton,” “Dragonfly” and “Havex” operations sponsored by Russia against multiple energy infrastructures demonstrate this approach. These cyber attacks resulted in malware being installed on more than 17,000 devices in the United States and abroad, including industrial control systems/supervisory control and data acquisition controllers used by power and energy companies. Importantly, Robert M. Lee, CEO of Dragos, described Triton’s infiltration into the safety system of a large petrochemical refinery as “the first piece of malware specifically designed to kill people.”
These vulnerabilities, whether native or inserted, are typically operationalized in legacy systems that were not designed to be secure, further increasing the vulnerability of critical infrastructure supply chains.
It is extremely difficult to perform consequence management of defense and energy supply chains and enterprises. Current operations, manufacturing and supply chains lack any semblance of a comprehensive risk register that would prioritize courses of action to protect enterprises. Today’s service level agreements for IT systems typically do not take into account the growing risks to defense and energy sectors.
There is a national security imperative to make U.S. supply chains more resilient and cyber-secure. In February 2022, the Department of Defense (DoD) issued a report entitled “Securing Defense-Critical Supply Chains” in response to President Biden’s Executive Order 14017, Executive Order on America’s Supply Chains. This report states, “Our work to build resilient, competitive, and sustainable supply chains will be a long-term campaign.”
Microelectronics supply chains are critical to national security and economic prosperity. They also represent one of the most challenging defense-critical supply chains to secure because of their global reach and contributions from both friendly and unfriendly nations. Defense, commercial and critical infrastructure sectors depend on a diverse supply of microelectronics products manufactured in a global ecosystem.
Building resilient, competitive and sustainable supply chains requires significant research, development and deployment efforts encompassing the best expertise of government, industry, academia and international organizations.
Production of these microelectronics is complex and typically follows a process of product design, fabrication (lithographic patterning and manufacturing of silicon die on a common substrate involving over 500 discrete processing steps), packaging, assembly, testing and quality control.
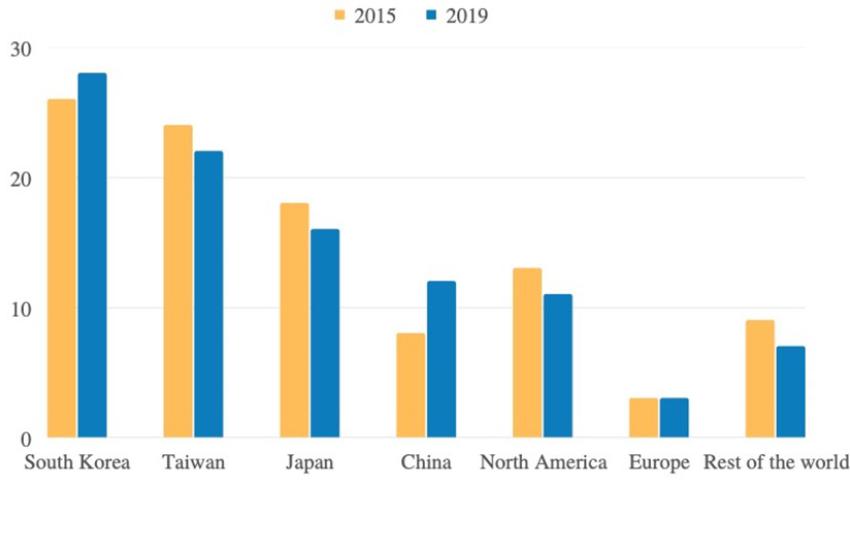
The microelectronics supply chain is globally dispersed, and much of the manufacturing is centralized in the Asia-Pacific region (see figure below). As summarized in the DoD report, the size and complexity of the global microelectronics supply chain can be inferred from the fact that more than 10,000 large microelectronics distribution companies are dispersed globally and serve as distribution points for over 500,000 microelectronics components. These supply chains have little or no traceable integrity and often cannot be trusted, which presents a profound challenge to national security.
These microelectronic supply chains and technologies are a central component to achieving DoD advance capabilities. Thus, questions of extreme importance to the nation’s defense and U.S. national security are: 1) How can we secure the microelectronic industry? 2) How can we introduce trusted traceable integrity into the global microelectronic supply chain?
In other words, when the U.S. receives chips, motherboards or components from any manufacturer in the world, including potential global adversaries, how can we validate and verify the integrity of the electronics prior to using them in critical infrastructure? Here are two key approaches that support the U.S. microelectronics industry to verifiable security properties and guarantees of physical functions. These principles offer U.S. manufacturers guidance on how to identify, mitigate and nullify potential weaknesses or faults in supplied parts—even those introduced intentionally. This approach results in quantifiable assurance for microelectronic supply chains.
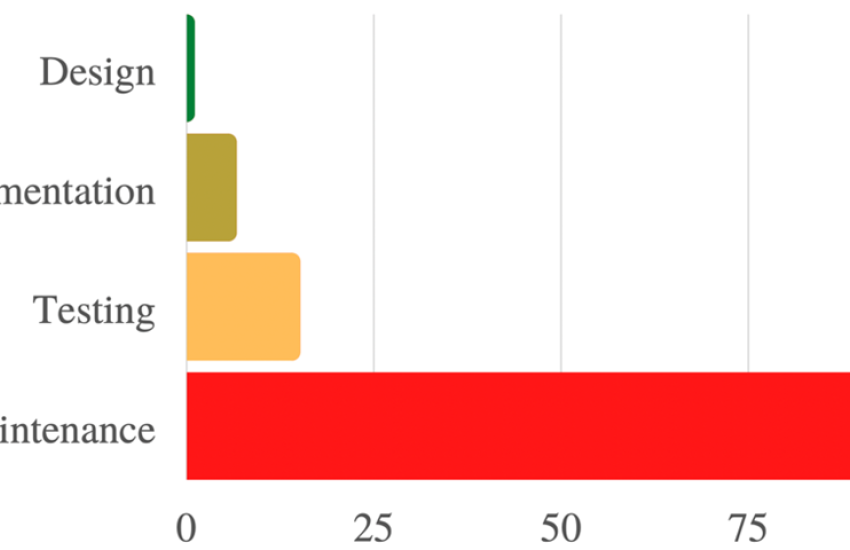
What are the building blocks required for defense-critical supply chains? First, develop formal cybersecurity design specifications and verification for the microelectronics industry (design for cybersecurity). By employing a new process for formal design specification and verification that spans implementation, integration and operation, potential adversary attack vectors are significantly diminished before implementation and deployment and providing security guarantees (e.g., integrity of the design file) that are propagated throughout the process. Moreover, eliminating or mitigating vulnerabilities earlier in the design stage is cost effective (see figure below). This may involve not only the design of the parts, sub-assemblies and products, but also the critical supply chain processes involved in sourcing, manufacturing and delivering the final product to end customers.
Typically, 90% or more of the life-cycle cost of sourcing, manufacturing and servicing is locked in the design stage of the product and supply chain, limiting opportunities for improvements later in the life cycle. Getting the design right from the beginning is critical. Given the significant new investments in the semiconductor industry over the coming years, this is the right opportunity to include formal design specification and verification in the next-generation manufacturing systems.
A design specification based on formal models entails the following steps: a) define the components of a system along with its interfaces (e.g., communication port); b) identify the connected components within the system; c) define the desired security properties (e.g., authentication, encrypted connections) and productivity properties (e.g., component input and output constraints); and d) verify that a design adheres to these defined properties. This formalism enables behavioral analysis of implementations, operations and “digital twins” of real systems to verify the required security properties.
Microelectronics-specific models can be used to verify and validate properties throughout the planning and design phases of supply chain integration to demonstrate the impacts of attacks, defenses and control system faults and to identify the costs associated with design tradeoffs due to security risks and mitigations. Formal design specification and verification also provides the microelectronic industry an avenue for explainability of security decisions across the supply chain and mitigation of vulnerabilities at the design stage.
Second, traceable integrity must be incorporated into the microelectronic supply chain. Microelectronics manufacturers have requirements beyond their individual plants that extend to their entire supply chain network. This supply chain network is a high-value target for adversaries as it serves as the conduit for proprietary intellectual property and sensitive commercial/operational data. It is also an ideal injection point for untrusted components/materials. Hence, we must develop and deploy innovations that provide end-to-end traceable integrity of the final product throughout the supply chain.
Relative cost to fix software defects
A cyber-physical passport architecture should be developed and deployed to capture design details, equipment status, product history and energy consumption and emissions profiles using a unifying data model, enabling interoperability and optimization across suppliers or original equipment manufacturers of various sizes and complexity. The cyber-physical passport is a foundational identity and activity validation element within a framework designed to support multiple parties.
For example, the key element of provenance for the supply chain networks is a single manufactured “part.” The provenance data relating to a part, such as its components, origin, design, manufacturer, software associated with the manufacturing process, data related to the manufacturing process, quality control data, ambient data, energy and emissions efficiency, etc., must all be securely captured and stored in the local manufacturing node. That information can be further used for analysis by employing privacy-preserving techniques across multiple supply chain nodes to infer overarching properties such as productivity, product integrity, quality and energy efficiency of the manufacturing process.
However, this information is rarely available for parts that originate from untrusted nodes in the global supply chain. In such cases, untracked and tracked components are analyzed when reaching controlled supply chain nodes and the results of such analysis are recorded in a cyber-physical passport to enable further integrity verification across the supply chain.
These cyber innovations can be applied to microelectronic manufacturing and semiconductor fabrication to prevent unauthorized changes to the microelectronic manufacturing and/or to verify the integrity of the design. The cyber-physical passport automatically collects provenance information and analysis artifacts that enhance the quality of products, improve productivity of systems, reduce energy consumption and significantly increase the cybersecurity of systems, operations and supply chains.
Securing defense-critical supply chains built on resilient and sustainable microelectronics fabrication and deployment is a national imperative and requires an investment in basic and applied research, development and deployment into industries in and out of the defense industrial base. Critical next steps include the development of pilots for revolutionary concepts in a new formal verification model and the cyber-physical concept for chain of custody. Critical infrastructure leadership should act with a sense of urgency. Working in conjunction with the undersecretary for Acquisition and Sustainment, the assistant secretary of defense for Research and Engineering should establish pilot programs with the Defense Advanced Research Projects Agency and the service labs to build and test both concepts in legacy and new system development. Additionally, the Pentagon may be aware that an existing Manufacturing Innovation Institute is piloting, with the semiconductor industry, cyber innovations to provide verifiable security properties and guarantees of physical functions to build a more cyber-secure, resilient and efficient microelectronics supply chain. This work is partially funded by the Department of Energy and executed at the Cybersecurity Manufacturing Innovation Institute (CyManII).
While all these efforts are early in development, they can be expedited as a national security imperative. Congress should review the results of these pilots and provide authority and funding to scale these architectural constructs on the nation’s highest defense priorities. The Semiconductor Industry Association recognizes that the industry needs to invest an astounding $3 trillion in research and development and capital expenditure over the coming decade to meet increasing demands for semiconductors. It is imperative to leverage these investments and emerging cybersecurity innovations to build risk-resilient high-technology supply chains from design to manufacture to operation. Designing supply chains for resilience is likely to be a much more cost-effective and profitable strategy than trying to retrofit existing ones.
Dr. Howard D. Grimes is the CEO of the Cybersecurity Manufacturing Innovation Institute (CyManII), which is revitalizing U.S. manufacturing through next-generation cybersecurity architectures. Grimes is an elected fellow of the American Association for the Advancement of Science with over 60 peer-reviewed publications, multiple op-eds and two patents.
Dr. Gabriela F. Ciocarlie is an associate professor in the Department of Electrical and Computer Engineering at University of Texas at San Antonio and a vice president for securing manufacturing and secure manufacturing architecture for CyManII.Robert Butler serves as the managing director for Cyber Strategies LLC. Butler is a retired U.S. Air Force colonel and a former member of the Defense Department’s Senior Executive Service.
Wayne E. Austad is the chief technology officer for National and Homeland Security Directorate at the Idaho National Laboratory. Austad is the chief research and development officer for CyManII headquartered at the University of Texas San Antonio.
The opinions expressed in this article are not to be construed as official or reflecting the views of AFCEA International.
Acknowledgements: This material is partially based upon work supported by the U.S. Department of Energy’s Office of Energy Efficiency and Renewable Energy under the Advanced Manufacturing Office Award Number DE-EE0009046. The views expressed herein do not necessarily represent the views of the U.S. Department of Energy or the U.S. government.





Comments