Nontraditional Intelligence Sensors for Cyber Operation
The increasing volume and sophistication of cyber threats have made semiautomated tools and techniques critical in detecting and responding to potential risks. Cybersecurity sensors are designed to monitor networks, systems and applications for signs of suspicious activity based on rules established by network defenders. However, these sensors must be finely tuned to minimize false positives (when a false threat is detected) and miss false negatives (when a sensor does not detect a threat). Consequently, intelligence professionals may receive less relevant data for threat analysis, as the volume of alerts can overwhelm their capacity to analyze data.
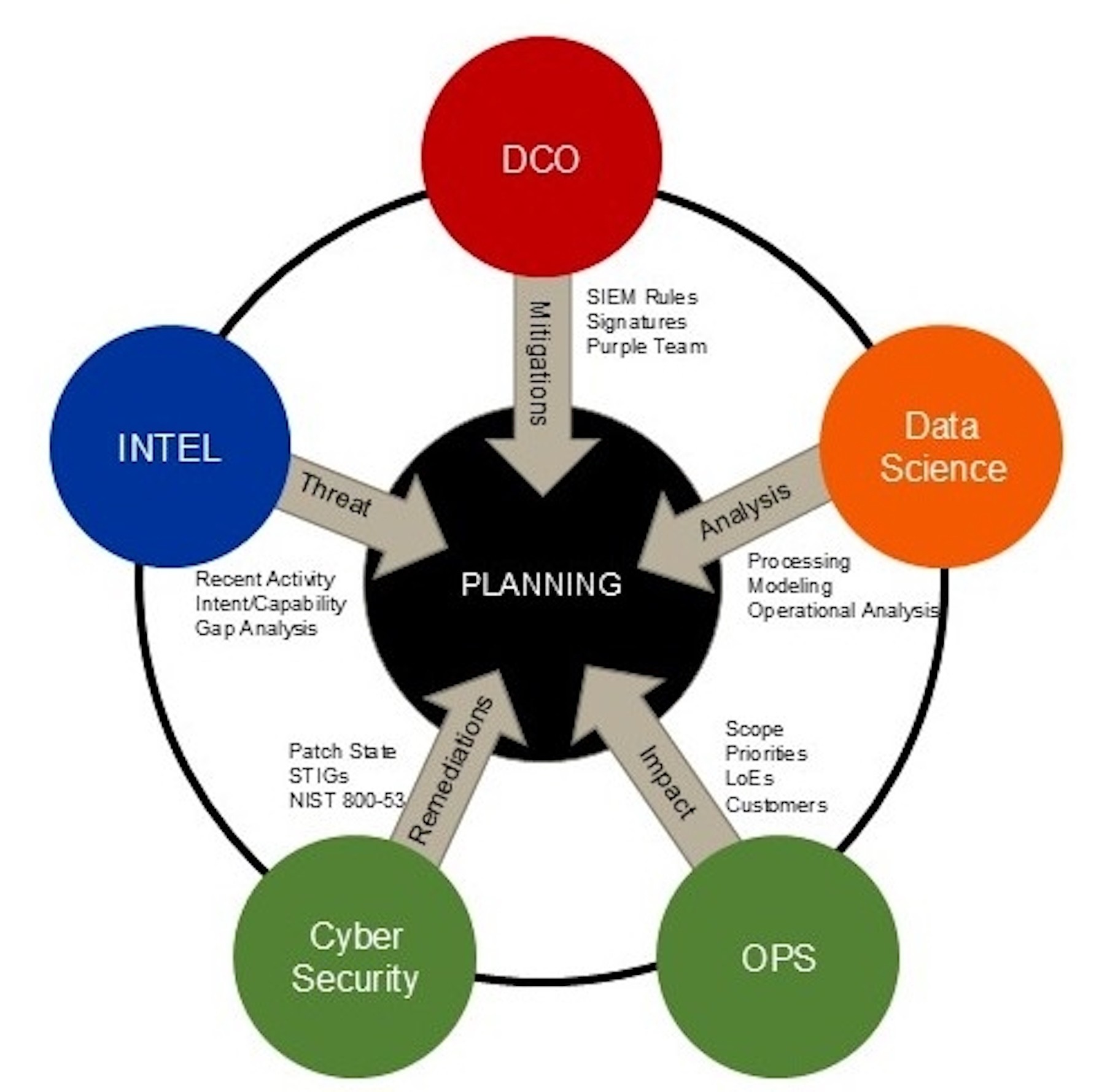
The importance of tuned sensors cannot be overstated. Intelligence professionals must integrate with cyber processes and understand sensor architecture—similar to traditional intelligence, surveillance and reconnaissance platforms—to tune sensors to prioritize threat tactics, techniques and procedures (TTPs). By assessing the architecture and aligning it with threat TTPs, intelligence professionals can assist network defenders and cyber decision-makers in identifying the best methods of resolving false positives and improving the operational collection of pertinent threats.
Effective sensor tuning is essential for reducing false positives and improving the accuracy of cyber threat intelligence. Tuning enables the refinement of cybersecurity sensors by network defenders and should be informed by the threat landscape and organizational needs to ensure protection measures are applicable and valid. Reducing false positives minimizes wasted time and resources and mitigates the risk of overlooking genuine threats. As a result, these misconfigurations can overwhelm security analysts and lead to missed threats, which leads to less impactful or incorrect intelligence analysis. Ultimately, sensor tuning is the responsibility of intelligence and cyber professionals collaborating to create the cyclical operations and intelligence process required to protect critical assets in the cyber domain that enable the advantage in all other domains.
Intelligence professionals should compare cybersecurity sensors to traditional land domain sensors like human intelligence (HUMINT) and signals intelligence (SIGINT), which require collaboration to ensure the most effective intelligence is collected to enable decision-makers. Bridging this gap will accelerate cyber and intelligence operational processes. Just as a HUMINT collector must carefully select and cultivate sources to gather relevant information, a cybersecurity sensor must be carefully tuned to detect and alert on relevant threats.
Furthermore, sensor tuning can be likened to the traditional intelligence cycle, where planning, collection, processing, analysis and dissemination are all critical components. Planning with cyber domain is similar for operations, as it requires the identification of terrain and how the threat intends to shape it, leading to sensor refinement and position to combat possible intrusions. Meanwhile, processing will analyze the collected data to evaluate threats within the terrain to prioritize remediation and deploy forces or equipment more efficiently. Finally, the dissemination phase involves providing relevant and actionable intelligence to decision-makers for rapid reactions regarding maneuvering assets on the network.
Using cybersecurity sensors as nontraditional intelligence sources offers a unique opportunity to enhance cybersecurity posture and support the cyber mission force. By leveraging these systems, cyber and intelligence professionals gain adversarial TTPs and use them to respond quickly and efficiently to address the risks. Strategies to reduce false positives and improve the accuracy of cybersecurity sensors should include internal adjustments and collaboration with external partners.
Cybersecurity sensors provide intelligence professionals with benefits compared to traditional intelligence collection platforms. The ability for cyber sensors to detect in real-time enables intelligence analysis to be actionable immediately and cyber defenders to achieve the objective rapidly. The sensors allow better visibility of the entire domain because they are interconnected through multiple systems and networks spanning multiple geographic areas. However, they also present unique challenges, such as the need for careful tuning to minimize false positives and the requirement for specialized expertise to analyze and interpret the data.
A critical factor in sensor tuning is documenting the measures of effectiveness and using the results to reduce false negatives while managing false positives. Furthermore, a singular standard being applied across the domain will enable a baseline of detection accuracy and response efficiency and can be aligned with evolving threat tactics. Future research should explore how the U.S. Department of Defense can leverage machine learning that seeks human approval and then make the sensor adjustments, adversarial tactics to improve evasion detection and cross-domain intelligence integration to enhance adaptability. Additionally, examining adversarial obfuscation TTPs will provide insights into optimizing sensor tuning against threats. Further study into cross-domain intelligence integration—leveraging data from cyber, SIGINT and HUMINT—can enhance sensor adaptability. Lastly, research into automation and artificial intelligence-driven sensor optimization will be instrumental in cybersecurity operations remaining proactive in a complex threat landscape.
In conclusion, tuning sensors is critical to effective cybersecurity operations and requires collaboration between intelligence and cyber professionals. By calibrating sensors using intelligence threat data from the organic network, the relevant threats can be deterred and reduce analyst burnout from focusing on the infinite number of threats in the domain. The comparison between network defense sensor tuning and traditional intelligence collection platforms is evident, as careful planning, collection, processing, analysis and dissemination are all foundations for a successful process. Using cybersecurity systems as nontraditional intelligence sensors allows for an organic network’s threat picture to be obtained and integrated into a common operating picture to drive commanders’ decision-making in improving defenses.
CW2 Travis M. Whitesel is an active-duty Army cyber warrant officer. Whitesel graduated from American Military University with his master’s degree in national security studies with a concentration in cyber operations in February 2023. He is pursuing a doctorate in cybersecurity at National University and is currently NETCOM G2’s senior technical advisor and serving as Regional Cyber Center intelligence support element at Fort Huachuca, Arizona. He can be contacted at travis.m.whitesel.mil@army.mil.
CW2 Jeff B. Newsome is an active-duty Army military intelligence warrant officer. Newsome graduated from American Military University with his master’s degree in intelligence operations with a concentration in homeland security. He is pursuing a doctorate in strategic Intelligence. He is currently the cyber intel section chief for Regional Cyber Center-E, NETCOM, U.S. Army Cyber Command at Fort Huachuca, Arizona. He can be contacted at jeff.b.newsome.mil@army.mil.
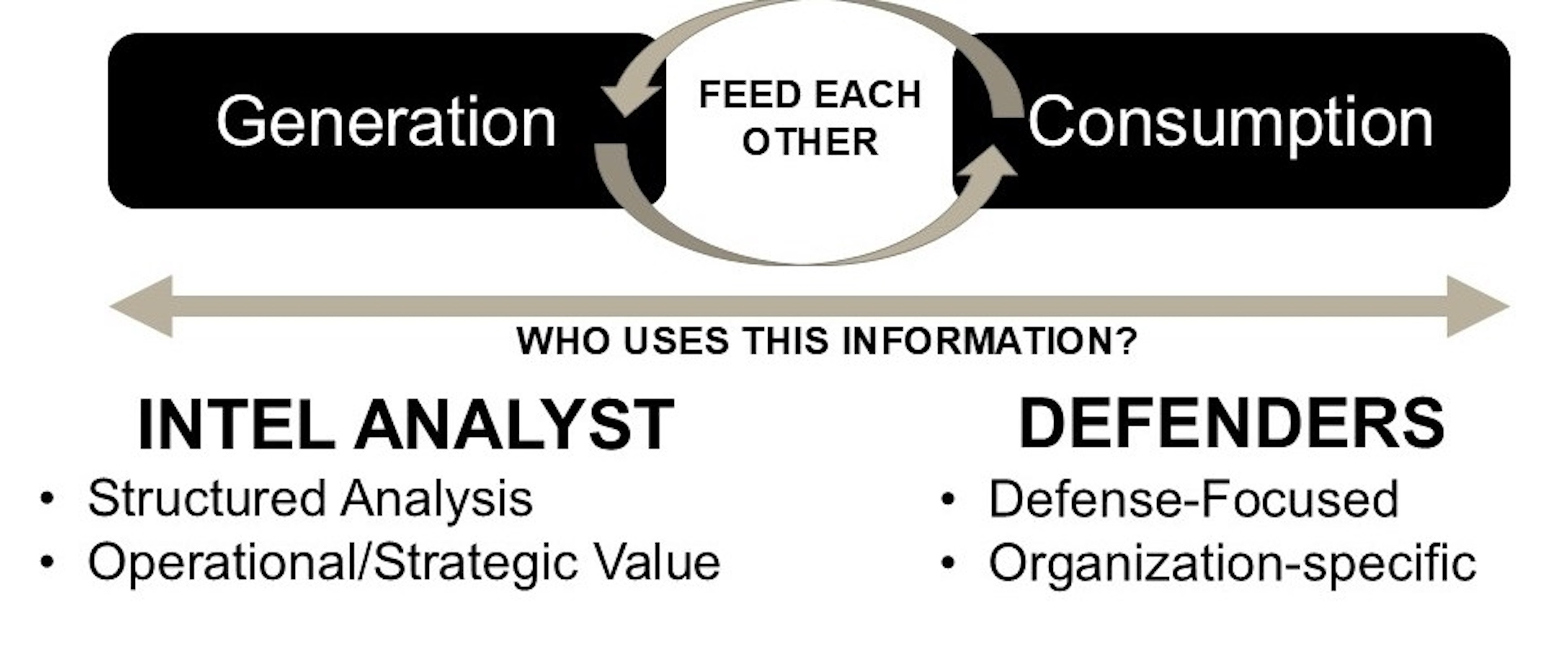
Intelligence professionals must understand sensor architecture to tune sensors to prioritize threat tactics, techniques and procedures (TTPs).
Travis M. Whitesel and Joseph Rudell, NETCOM G2






Comments