Tips for Zero Trust Strategy Implementation Leads
Guided by the Office of Management and Budget's Memorandum M-22-09, each federal agency has had to recently appoint a zero-trust lead to start the organization's journey into applying the advanced cybersecurity measures. Successful zero trust implementation requires executive or mission sponsorship. For those wondering how zero trust leads can build a program that sustains executive sponsorship over the life of the program, we suggest starting first with data protection, as data is the lifeblood of any organization. Starting with data also allows you to answer your agency leadership’s question of how well did the zero-trust program protect the agency’s most vital asset–its data?

In starting with the data pillar—it is “first among equals”—the zero-trust implementation lead should partner with the agency’s “data stewards” to ensure critical mission data is always available to support mission functions and is never compromised and never falls into the wrong hands. In turn, the data stewards’ role on the zero trust team is to operate a data governance organizational framework with key roles and responsibilities.

Data stewards are the product owners of the mission data. They “own” the data, which is based on mission function, and they control who has or doesn’t have access to that data. The data stewards ensure the data is always protected—whether it is at rest or in transit, wherever the data is located and whenever it is being used. In addition, they understand how data is used across the various mission functions and adjust access or permissions accordingly based on the ever-changing mission usage needs.
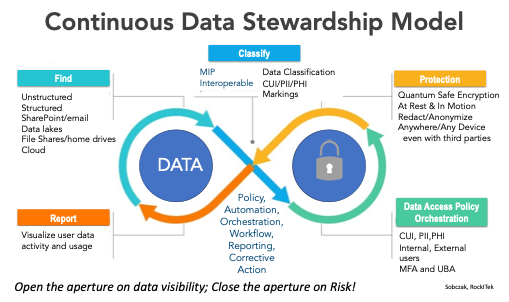
The data steward, partnered with an agile information technology team, can then implement these data protection and usage policies, with automation playing a key role in their implementation. They can use an iterative playbook to discover, classify and protect the data according to its sensitivity. They can monitor and manage the use of the data on a continuous basis.
Having precision insights into mission data flows/usage is a key ingredient for effective data stewardship. Moreover, continuous monitoring enables ongoing mission and data operations analysis, which is essential for deciding data protection, data access and data usage.
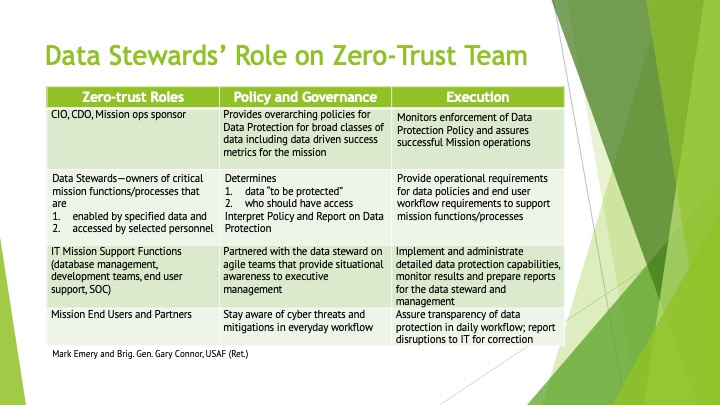
We suggest critical success criteria for the data steward to include:
- The mission leadership assigns the data steward for each critical data set; the mission leader can be informed by the discovery, classify, protect and monitor processes implemented by a chief information officer’s operations team;
- Consider the chief data officer as the quarterback, or main orchestrator, to maintain alignment amongst the data stewards;
- All zero trust stakeholders—chief information officer, chief data officer, mission owner, information technology operations—need to agree with the data steward’s authority to set requirements for data security implementation details throughout the data life cycle; and
- The data steward has experience working with private, sensitive and open data.
Data stewardship combines accountability by data owner with mission or organizational policy automation enabled by technology, to ensure the right data is used at the right time by the right people or applications for the mission.
In addition, the chief information officer operations team can jumpstart the data protection life cycle with protections set to “open,” and then apply the data usage information to assist mission leadership and the chief data officer in appointing the appropriate data stewards to implement data protection policies. With that, data can be protected for its entire life cycle, from creation to archival, and data owners can visualize data use and thus tailor data access to only those who require it.
By Mark Emery and Ret. Brig. Gen. Gary Connor, USAF.





Comments