Panel: Equipping the Cyber Force Means Giving Them Tools To Understand What They Manage
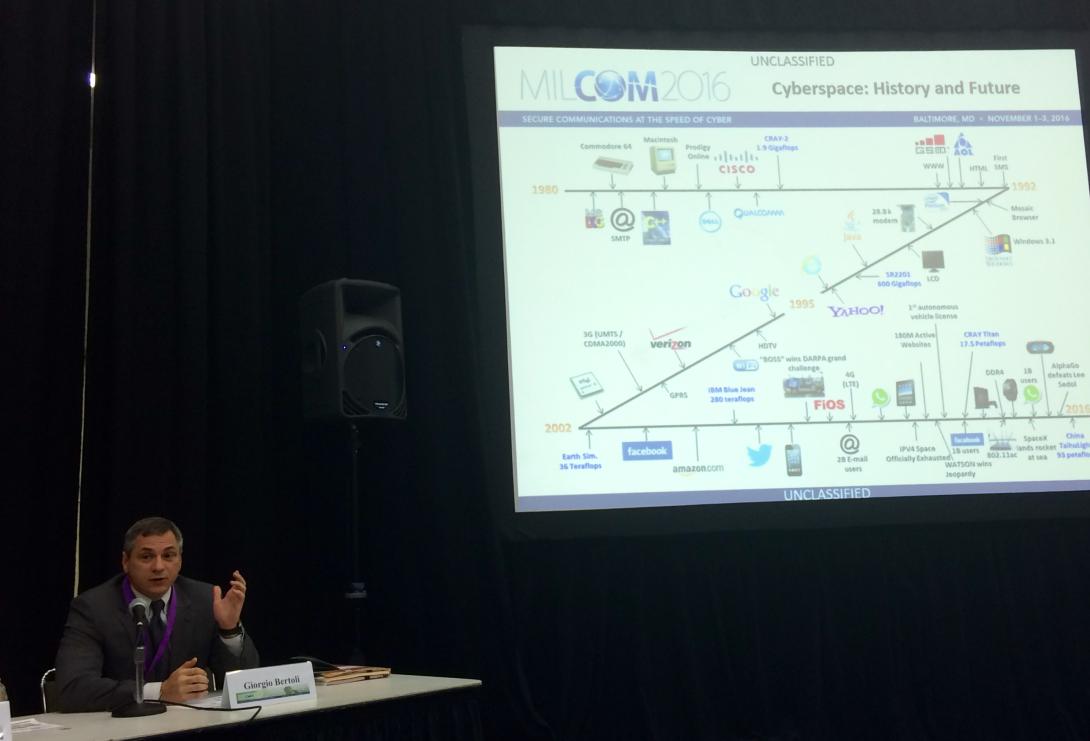
The history of the Internet as we know it today doesn’t really date back that far. Some 25 years, really. But what is both enticing and concerning is that the rate of change in this arena constantly is speeding up, making it difficult to forecast where technology will go next.
The history of the Internet as we know it today doesn’t really date back that far. Some 25 years, really.
But what is both enticing and concerning is that the rate of change in this arena constantly is speeding up, making it difficult to forecast where technology will go next, said Giorgio Bertoli, senior scientific technical manager for offensive cyber at the Intelligence and Information Warfare Directorate (I2WD) at the Army’s Communications-Electronics Research, Development and Engineering Center (CERDEC).
In #cyberspace, U.S. military has more problems than solutions—but that's why we're all here at #MILCOM, says Giorgio Bertoli from @CERDEC
— Sandra Jontz (@jontz_signalmag) November 2, 2016
What took Facebook a decade to accomplish has been achieved by follow-on social app companies in a fraction of that time, Bertoli said during a presentation Wednesday at MILCOM 2016, a premier conference focusing on military communications. MILCOM takes place November 1-3 at the Baltimore Convention Center and is co-hosted by AFCEA International and the Institute of Electrical and Electronics Engineers, or IEEE.
Cyberspace is becoming more complex, testing the U.S. Army’s research, development and engineering community to keep pace and surpass threats. It has become the most dynamic and challenging of the U.S. military’s warfighting domains, said Michael Lombardi, deputy director at CERDEC’s I2WD.
Some of the biggest challenges involve just keeping up with technology, said Donald Coulter, a computer scientist and team lead for trusted systems and networks with CERDEC’s Space and Terrestrial Communications Directorate.
The speed of cyber is much faster than what humans can compete with, which is driving researchers’ efforts to perfect multi-factor authentication, automation and artificial intelligence and technologies that will teach machines what analysts do so machines can take over, said Chuck Smith with the U.S. Army Research Laboratory (ARL).
Major research themes within the ARL center on the following: supply chain management; moving target and dynamic cyber defense; insider threat, information security; continuous monitoring; hardware-rooted security in mobile devices; designed-in cybersecurity; cyber situational awareness; cyber attack response and recovery; cyber attack detection and analysis; cloud computing; building trustworthy resilient systems, and big data analytics, Smith offered.
“We’re looking for technologies that can help us get a better understanding of what’s going on out there,” Smith said. “You can’t manage what you don’t understand.”







Comments