New Tools Keep Terrorists at Bay
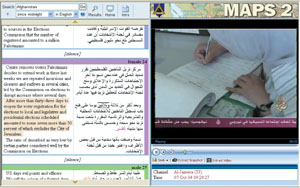 |
| The Multimedia Art Processing System (MAPS) is designed to automatically translate and transcribe foreign media broadcasts for analysis. The system's translation software provides a rough translation of a broadcast. MAPS can translate up to six media feeds simultaneously and perform key-word searches through live and recorded broadcasts. |
Stitched video, ground radar and virtual simulations sharpen security and speed emergency response.
Smart surveillance systems soon will make it difficult for militants to infiltrate mass transit facilities and secure installations. These technologies, along with advanced foreign-media monitoring and first-responder training applications, provide government and law enforcement organizations with a crucial edge against terrorism.
The United States and its allies are engaged in a war against an elusive international enemy who strikes suddenly and retreats into the shadows. The careful and precise use of technology to detect and counter such attacks is a key weapon in this struggle. Intelligence-gathering tools allow analysts to detect trends, while surveillance and monitoring applications help enforcement agencies intercept terrorists in transit before they can strike. And should an attack occur, advanced training techniques allow emergency response personnel to minimize its effects.
Researching, developing and distributing these security applications is the responsibility of the Technical Support Working Group (TSWG), an interagency U.S. government research organization. The working group collects information from law enforcement and federal agencies concerning their counterterrorism requirements. It then solicits bids from private industry for applications. According to Jeffrey David, deputy director of the U.S. Defense Department’s Combating Terrorism Technology Support Office, Washington, D.C., which manages the TSWG, these programs can vary widely in their complexity, duration, scale and cost.
Several new technologies under development include the Multimedia Alert Processing System (MAPS), the Blanket of Video Cameras (BVC), the Mass Transit Surveillance System, ground surveillance radar and the Scenario-Based Interactive Exercise Simulation.
MAPS is a desktop computer-based system that automatically translates and transcribes foreign media broadcasts. Designed for use by intelligence analysts, MAPS presents a media broadcast as three columns on a monitor. For example, an Al-Jazeera broadcast would present an English transcript on the left, an Arabic transcription in the center and the actual media broadcast on the right. Users can select and search data by key words, which are highlighted in the transcript text.
The initial translation is only about 40 percent accurate. Its purpose is to provide the analyst with the overall gist of the broadcast. However, David notes that this level of accuracy is better than that of other available mechanical translation tools. If the broadcast is of interest, the analyst can request a full translation from the National Virtual Translation Center.
Automated translation speeds are slightly below real time—there is a 5-minute delay as the software translates the broadcast. MAPS also can simultaneously process up to six different media feeds. Additional funding is being sought to improve the literal translation capability. David notes that the military has been testing two prototypes for almost a year.
Besides media searches, the working group is funding programs, such as BVC, to protect facilities and infrastructure. This video surveillance system is designed to provide site security personnel with situational awareness through interlocked ground and aerial video cameras. Designed for force protection and perimeter monitoring, it integrates stationary cameras and motion sensors with aerial and mobile platforms.
The BVC’s base technology is built around the Sarnoff Corporation’s Video Flashlight Technology. According to David, a facility is first mapped with a laser radar system. The cameras are then placed in the facility to provide interlocking coverage. The system allows operators to track intruders through a facility. He notes that a common theme is not only detecting intrusions but also observing and assessing the situation. Instead of sending security personnel to the point where the alarm occurred, they can be guided to interdict the intruders within the facility.
The technology plugs into existing security systems. It provides both visual and audible alarms to alert operators to an intrusion, and sensor settings can be varied in different areas depending on the required security levels. Instead of directing camera feeds through multiple monitors, the BVC digitally stitches all of the facility’s camera imagery into a single view. Rather than track intruders from camera to camera, the system can monitor their progress on a single screen providing an integrated “God’s eye view,” he says.
A prototype BVC system is operating at Eglin Air Force Base, Florida, for force protection testing. David notes that the U.S. Air Force is experimenting with different options and techniques for its use. The system also is being compared against a standard fixed camera system at an overseas Defense Department facility.
A related application using the base BVC technology is the Mass Transit Surveillance System being developed by the University of Minnesota. It is an integrated monitoring and alert system designed to detect anomalous human behavior in mass transit terminals. The system uses multiple streams of video feeds to provide a centralized security and emergency response capability.
The technology integrates various video streams into a single screen-picture and provides audio and visual alerts when certain behavior is identified. David notes that it was designed originally to track abandoned packages and evolved into a system to observe crowd movement. But the system is still in its infancy, and the algorithms for the tracking software are currently under development. The program will require several more years of development, he says.
The Mass Transit Surveillance System is intended to supplement existing security grids because vital areas need nearly complete coverage. This will necessitate a combination of new and existing cameras tied together to provide a common operating display. The system must be adaptable to monitor a variety of venues such as subway and light-rail stations, bus terminals, tunnels and bridges.
Another TSWG program uses existing ground surveillance radar to provide intrusion detection at commercial airports. The working group and the Transportation Security Administration are jointly modifying existing Airport Surface Detection Equipment (ASDE-3) ground surveillance radars for this purpose. These systems are used to track the movement of aircraft as they taxi and of vehicles on airport flight lines.
David explains that the modifications consist of processing the radar data so that it detects only humans and specific types of objects, such as boats, inside and around the airport perimeter. Like the other systems, the radar surveillance equipment will provide operators with a single integrated operational picture of the airport grounds. This allows intruders to be detected and tracked for interception by security forces. A prototype system is being evaluated at a major U.S. airport, he says.
The TSWG also is developing a virtual training system for first responders. The Scenario-Based Interactive Exercise Simulation is designed to train groups of geographically dispersed personnel efficiently and to reduce travel and training expenses. The system uses a multiplayer, online gaming technology incorporating virtual reality techniques and interactive simulation. The role-based scenarios are intended to familiarize participants with agency roles, assets and response protocols.
David notes that end users for the system range from the Defense Department to first responders. The goal is to allow almost everyone involved in combating terrorism to use this tool, he says. The software will allow the simulation of events such as chemical, biological, radiological, nuclear and explosive attacks in realistic environments. Key highlights of the technology include a realistic synthetic environment that replicates cities, ports and trains. Virtual participants in the simulation wear protective equipment and other mission-specific gear to create a more realistic experience.
The content of the simulation is consistent with regional and national exercise programs. The software features an authoring capability, allowing users such as fire chiefs to customize scenarios to meet specific needs. Scenarios and operational environments will be available via pull-down menus. Users can select from cities such as New York and Philadelphia or a generic urban area.
Users interface with the simulation through a game-style controller similar to a Microsoft Xbox. The software resides in a central server, and participants receive a compact disc to install the software on their desktop or laptop computers. The discs allow users to log in and participate in the exercises. The software is designed to operate on most personal computers. David notes that while the simulation graphics will be better on a desktop machine, bandwidth is a major consideration. The program allows users with 56-kilobit dial-up modems to participate.
The system currently is in its proof-of-concept phase and will undergo another year of development. Although the technology is designed for multiple users, David notes that initial tests were limited to small groups. The goal is to permit hundreds or even thousands of users to participate concurrently in an exercise, he says. Medium-size exercises are planned within the next six months, and a large-scale event involving multiple facilities in different states will occur within the next year.
Snapshot of the Technical Support Working Group The Technical Support Working Group (TSWG) is a research, development and prototyping organization for anti-terrorism communities in U.S. and allied governments. Its purpose is to identify, develop and field the best technologies, explains Jeffrey David, deputy director of the U.S. Defense Department’s Combating Terrorism Technology Support Office, Washington, D.C., which manages the TSWG. “It’s about finding the best solutions from industry, academia and foreign partners, then getting new technologies or new technical capabilities developed and fielded,” he says. Originating as a policy discussion group in 1982, the TSWG received its first official funding in 1986. The U.S. State Department’s Coordinator for Counterterrorism and the Defense Department’s Assistant Secretary of Defense for Special Operations and Low Intensity Conflict oversee the organization. David notes that although the working group is intended to expedite new technologies to users in the field, it follows government contracting rules. But because its projects are usually smaller in scale than Defense Department programs, they generally enter service more quickly. “We’re not building F-16s. We are making something a trooper can carry on his back,” he says. Every January, the working group’s 350 members, who are drawn from all branches of the government, are briefed by the intelligence and law enforcement communities on the latest threat assessments. User subgroups then meet to identify and prioritize requirements. During the months of January and February, this group consolidates its priorities. David notes that TSWG programs tend to be short-term and more user-focused than other large government initiatives. In late February, broad agency announcements (BAAs) are released to alert private industry about the TSWG’s requirements for the upcoming year. The best bid submissions are then selected during the following months. David notes that the working group runs many competitions concurrently. “It’s not like we do a request for proposals and spend lots of time reviewing it. We do one BAA with 20 to 60 concurrent requirements. When the money comes in, we award them. Those projects may be $100,000, or they may be several million dollars. They may be six months long, or they may be three or four years long. Every one is different because every requirement is different,” he says. |
Web Resources
Technical Support Working Group: www.tswg.gov/tswg/home/home.htm
Office of the Assistant Secretary of Defense for Special Operations and Low Intensity Conflict: www.defenselink.mil/policy/solic
U.S. State Department Coordinator for Counterterrorism: www.state.gov/s/ct




Comments