Intelligence Community Embraces Virtual Collaboration
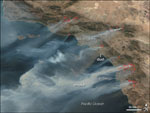 |
| This satellite image of Southern California wildfires was generated by the National Geospatial-Intelligence Agency (NGA) as a composite with descriptive overlays. Infrared hot spots that betrayed actual fires are highlighted in red. The NGA used new intelligence community virtual collaboration services to generate and distribute the images from its St. Louis facility to firefighters on the ground in the affected areas. |
The nature of intelligence community activities has been changed as increasing numbers of people adopt virtual collaboration tools and methodologies. A host of systems unleashed a handful of years ago has burgeoned into a new way of engaging in intelligence operations that is moving through the community.
Users set free to explore these new cyberspace systems have uncovered new capabilities and have driven the introduction of still more collaborative systems. Much of the expansion of virtual collaboration capabilities has been driven by the users, not by top-down fiat.
The result is that finished intelligence reports now are richer than before virtual collaboration was adopted. An issue is viewed through more than one perspective; and the overall effect is timelier, more agile and more accurate intelligence reporting to decision makers, says an intelligence official.
“We have made significant strides since 9/11,” declares John E. Hale, chief of service delivery for intelligence community enterprise solutions in the Office of the Director of National Intelligence (ODNI) Chief Information Officer (CIO). “When it comes to virtual collaboration in the intelligence community, I think we’re leaps and bounds ahead of the rest of the federal government. We jumped on virtual collaboration fairly early—we probably got lucky because we didn’t get burned, everything worked well—and users have really come in in full support of it.”
A spate of systems introduced in 2005 has spawned new adherents who in turn are changing the way that intelligence information is turned into products, particularly across agency lines. Hale believes that, as his office continues to evolve products and services, more barriers will fall.
Hale notes that when his office began to field virtual collaboration tools to intelligence community members, it did not provide a large amount of governance and guidance to the community. “We basically told them what they could and couldn’t do, but we didn’t necessarily tell them how they could use the tools to do their jobs,” he says. “We let the community as a whole decide the best way to use the capabilities to satisfy their mission.”
One prime example is Intellipedia (SIGNAL Magazine, October 2007). It is based on the same software package as the Internet’s Wikipedia online encyclopedia. But when Intellipedia was fielded, the intelligence community decided that it would not use it as an encyclopedia but instead as a place for live collaboration. Now, Intellipedia has more than 100,000 contributors across its domains. A large amount of these users are from the U.S. Defense Department, Hale reports.
Intellipedia has just been enhanced by the addition of a WYSIWYG editor, which stands for “what you see is what you get.” This provides easier functionality for users editing material by displaying their information in a format similar to the final output. Previously, users needed to know codes to make their information appear acceptable. To make information look good, users had to learn special markup capabilities. Hale relates that this upgrade allows even nontechnical users to edit Intellipedia content easily.
Low-level analysts and consumers, who tend to be digital natives, have not had a problem embracing these new collaboration tools, Hale says. More experienced intelligence community personnel, especially those who can be described as digital immigrants, were daunted by the prospect of learning a new language. Digital immigrants tend to have difficulty learning to play in the shared space, so this upgrade is part of an effort to tailor the cyberspace environment to suit their needs.
Intelligence virtual collaboration generates its best results with issues that transcend organizational boundaries, Hale warrants. This illustrates that the defining aspect for utility is not technical but cultural. This collaboration is finding its greatest adherents when bridging cultural barriers, not overcoming technical hurdles. Hale suggests that, because agency budgets tend to facilitate collaboration from within, agencies are gleaning benefits from virtual collaboration tools in common shared space that break down these barriers.
This revolution began in 2005 with the introduction of several collaboration services: Intellipedia, instant messaging across agency lines, a social bookmarking capability similar to del.icio.us, an enterprise search capability and enterprise blogs. Most of these services are used widely across the entire community. “There is no strong pocket of users that goes one way or the other,” Hale says. Intellipedia is the most widely used service.
Hale says that reaching critical mass—the point at which a service has enough participation to make it attractive to new users—took some time for these early systems. It took a year to reach the first major milestones. But, over the past two years, participation has increased tenfold. In late 2007 when Hale’s office launched iVideo, the intelligence community’s version of YouTube reached critical mass within 30 days of launching. Thousands of users were making active contributions every day, he relates.
“It’s been a culture shift in the fact that people are now willing to adopt these new services to get their job done,” he reflects.
For example, community members have embraced blogging. Hale offers that most of the blogs tend to be focused on a subject area in which a group of analysts share information about activities related to their focal area. Other blogs may focus on a specific event. This blogging realm is a self-policing community, Hale points out, so users only initiate blogs that will be considered relevant by their peers. It is very rare that any content needs to be removed, he adds.
One innovative use of intelligence virtual collaboration involved a domestic concern—
“If you don’t put really tight restrictions around it, the users are going to use [these tools innovatively] in ways that we as service providers could never imagine,” he says.
Most of the technological hurdles to virtual collaboration have been overcome, Hale says. The community contends with the same issues facing the commercial world—different browser versions, plug-ins and other mechanisms. Because the intelligence community comprises several agencies, many of those standards are established within individual agencies, and these differences must be overcome.
Hale states that the biggest hurdle has been cultural—convincing people to think topically rather than organizationally. “It’s a culture shift towards working in a shared space versus solely working in a vacuum.” His office has worked to overcome that hurdle by making the shared space as appealing and easy to use as possible.
“Our approach is, you give [community members] a good easy-to-use solution, and they will come,” Hale declares. “And, it’s working.”
With these new services receiving widespread acclaim and use, the community now has a wish list of new capabilities. Two in particular stand out. The first is for a Facebook or LinkedIn type of capability that would allow a user to profile him/herself and locate similar types of colleagues within the intelligence community. Within the past year, the ODNI has fielded A-Space, which Hale describes as the first push into that realm. It combines aspects of both Facebook and LinkedIn. A-Space’s major limitation is that it is available on only one network, so Hale’s office is looking to move that “out to the fringes” to build as large an audience as possible.
The other capability that is generating a wishful buzz among intelligence professionals is Twitter. This microblogging capability limits text length to 140 characters per post. So, a posting tends to represent a single thought instead of a presentation.
The intelligence community would use a Twitter capability differently from the public’s social approach. An intelligence Twitter might take the place of instant messaging. Hale points out that instant messaging involves point-to-point communication that dissolves into nothingness when the link is terminated. However, Twitter allows the same type of communication, but it also leaves a searchable record on the network. Hale says he is hoping for funding in the next fiscal year so that his office can build a pilot Twitter program.
The intelligence community is opting to build its own versions of these widely popular public capabilities for several reasons. Concerns about malware embedded in popular commercial social networks are valid, but those concerns would not be show stoppers, Hale offers, saying, “There are ways to mitigate those.” The main reason that the community does not use the services that exist in the public domain is physical data security. Hale observes that no one can state definitively where data will be stored. “Unless you have a specific agreement with that provider, you cannot guarantee where the data is going to reside, how the data is secured or how the data is backed up,” he explains. “These are all the basic requirements of the federal government for all of its data. The general public may not care where that server resides; but from a government perspective, we do care.”
When it comes to introducing new virtual collaboration systems, the intelligence community effectively has charged Hale’s office to proceed from concept to pilot to certified and accredited system in about 100 days—regardless of that particular system’s functions and goals, he points out. “Long gone are the days of the $50-million, five-year program that ultimately would end up with a solution that never actually met the first requirement. Now, we’re doing very rapid prototyping and piloting and then the certification and accreditation process—which is the one thing we face in the government that most commercial vendors do not have to deal with.”
One critical need the intelligence community requires from the commercial world is greater transparency about a product’s security. “In order for us to get things through that [acquisition] process that quickly, commercial products need to be a lot more transparent in their security posture,” Hale states. He adds that the community’s high-value data must be secured by the services appropriately, regardless of the type of service.
A large element of the security challenge comes from the transition from a compartmentalized need-to-know environment to a more open need-to-share one. Some collaboration services allow information to be shared among the broadest audience possible, while those same services also permit restricting data access to the most limited subset. Hale allows that some agencies or programs aim to lock down their information, while others seek openness. The community draws that line between need-to-know and need-to-share, he says. “It’s not a perfect thing; one of the things we’ve had to do is to push people to try to sway that line one way or the other.”
When a service is fielded to intelligence community users, Hale relates that his office must ensure three characteristics. The first is that the new service is not a burden to its users, or else they will not embrace it.
Another, and related, characteristic is that it is not a burden on the technological side. If it is too hard to implement, then those who are tasked with that role will not carry out its implementation. Issues include certification and accreditation, for example.
The third characteristic is that the service must not be a burden on the business side. A system must have licensing that permits the product to be used across myriad users.
Hale notes that his office has been pushing the commercial sector to embrace these three elements, and vendors largely have been receptive.




Comments