Sponsored: 2019 State of the Phish Report Reveals Troubling Trends, Shifting Impacts
It’s no secret that cybercriminals use email-based phishing prolifically, in both broad and targeted attacks.
Social engineering and its impacts on organizations worldwide are hot topics in infosec circles—for good reason. It’s no secret that cybercriminals use email-based phishing prolifically, in both broad and targeted attacks. But what are infosec teams—the boots on ground in the cyber war—experiencing in terms of impacts, and are they effectively managing risk?
The latest Proofpoint "State of the Phish Report" examines these topics via a series of infosec and end-user surveys, as well as analysis of proprietary data from its security awareness training platform. Key findings point to shifting trends and a need to focus end-user education efforts accordingly.
All Forms of Social Engineering Increased in 2018
Quarterly surveys of infosec professionals throughout 2018 generated nearly 15,000 responses and offered insights into the issues security teams are facing in the wake of social engineering attacks.
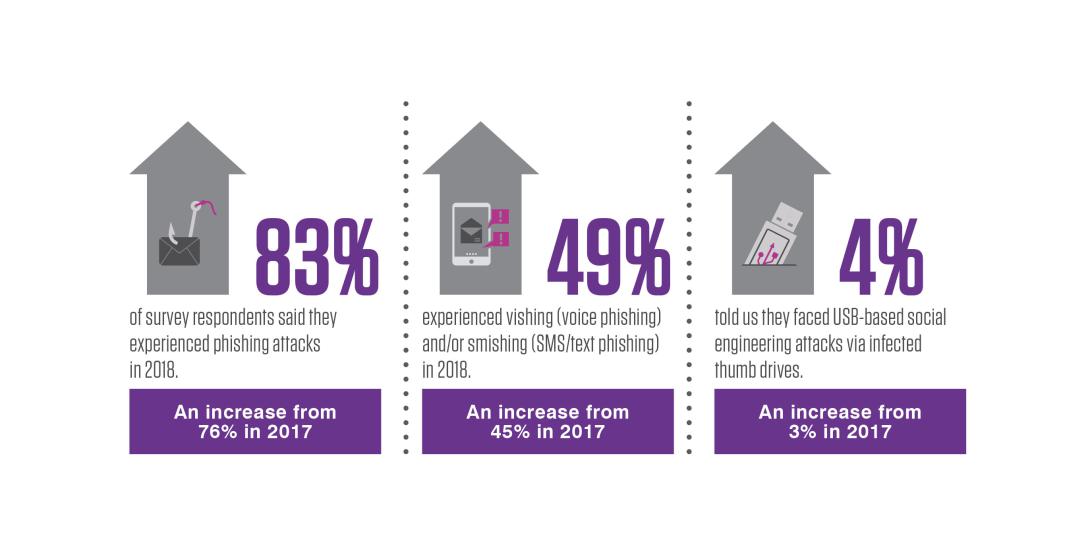
Overall, 83% of respondents said they experienced email-based phishing attacks in 2018, an increase from 76% in 2017. However, this wasn’t the only form of social engineering that was seen more often last year; respondents reported higher frequencies of smishing (SMS/text phishing), vishing (voice phishing), and even USB attacks.
Account Compromise Overtook Malware Infections as the Most Commonly Experience Phishing Impact
Proofpoint has been tracking infosec professionals’ stated phishing impacts for several years. Last year’s survey responses revealed an interesting (and concerning) trend: Reports of compromised accounts rose 70% over 2017, bypassing malware infections as the most commonly identified impact of successful phishing attacks.
As reflected in the chart, credential compromise has risen 280% since 2016. The report states that this increase is “of particular concern given that multiple services often sit behind a single password.” A recent Proofpoint study of major cloud service tenants shows how threat actors can leverage compromised credentials to their advantage across multiple platforms.
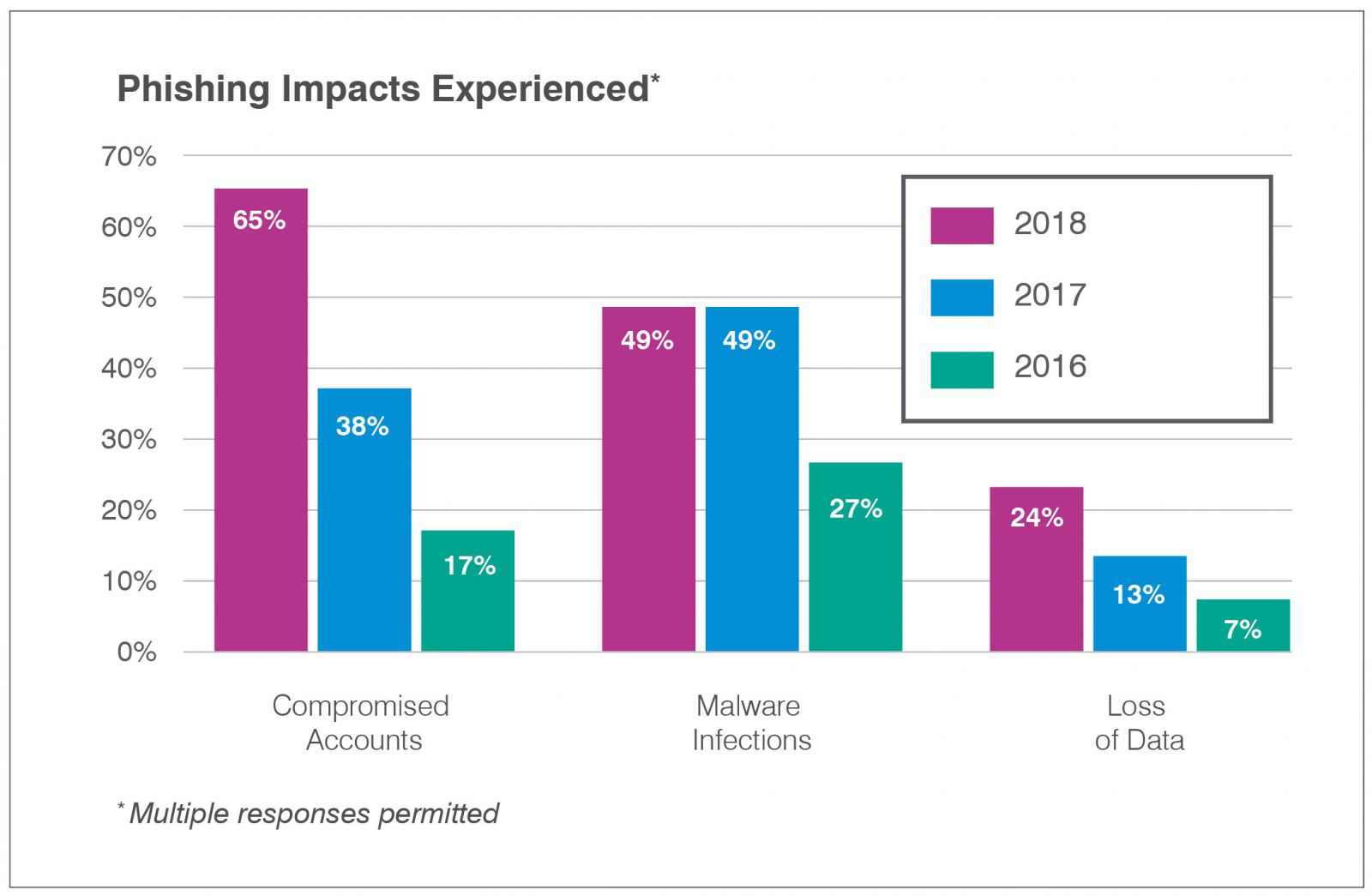
Still, it’s clear that account compromise isn’t the only problem infosec teams are dealing with following successful phishing attacks. Though reports of malware infections held steady between 2017 and 2018, they’ve risen more than 80% since 2016. And reports of data loss (a frequently under-reported outcome) more than tripled in two years. According to Proofpoint researchers, “the significant increases across all three categories since 2016 not only speak to the growing phishing threat, but also to organizations’ heightened awareness of—and attention to—the effect these attacks have on businesses.”
Organizations Should Target Security Awareness Training to Address Growing Threats
Of the social engineering attack methods noted here, it’s likely that organizations are only testing and training users on email-based threats. The attack landscape has shown cybercriminals’ tenacity and desire to utilize all possible channels to exploit end-user behaviors. Smishing, vishing, and USB attacks are difficult to track and stop from a purely technical standpoint, so it’s critical that organizations raise end-user awareness of these threats and train on best practices for spotting and avoiding attacks of this nature.
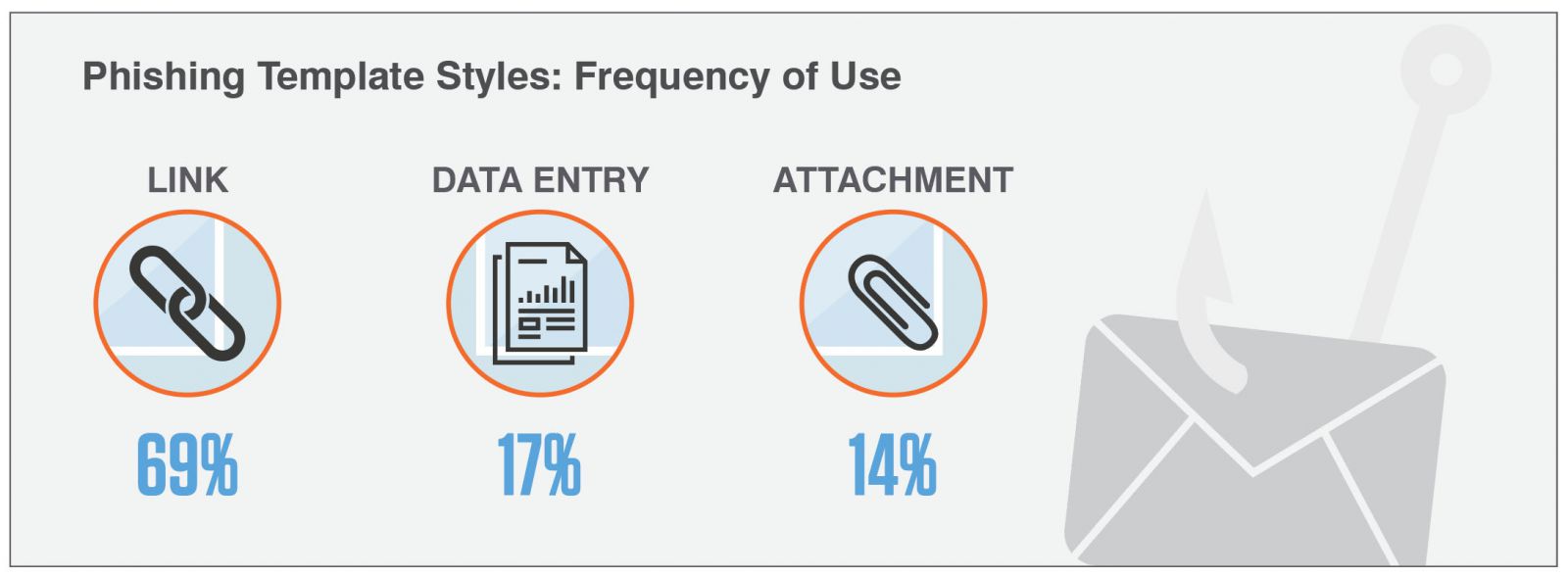
According to Proofpoint researchers, there’s also a gap on the phishing awareness training front. Data from the "State of the Phish Report" indicates that organizations infrequently use data entry-style simulated phishing attacks, which mimic credential phishing by prompting users to submit login names, passwords, or other sensitive data.
Of the tens of millions of phishing tests analyzed for the report, the vast majority assessed users on their vulnerability to links (see the illustration below). Though these exercises are certainly worthwhile, the numbers appear lopsided given the rise in credential phishing attacks. Proofpoint researchers exerted a strong recommendation that infosec teams look to trending attacks methods at large as well as those affecting their organizations in specific in order to “deliver the right training to the right people at the right time.”



Comments