Hunt the Cyber Threat— Before It Hunts You
The modern cyber threat landscape is quickly evolving. Today’s adversaries are scaling their operations, streamlining their tactics, and recycling and evolving their successful techniques to gain speed and stealth.
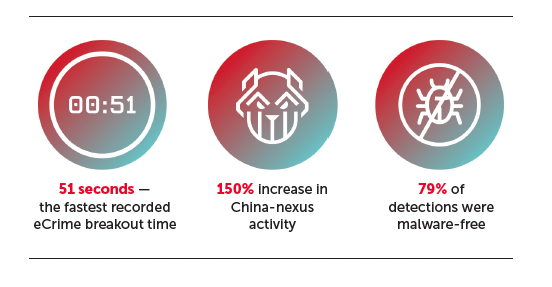
Many of these effective techniques rely less on malware and more on legitimate credentials and native tools to breach and navigate business environments. The CrowdStrike 2025 Global Threat Report states 79% of observed attacks in 2024 were malware-free. As adversaries change their tactics, cybersecurity teams must do the same.
In the modern era of cyber threats, adversaries could be quietly operating in your environment. And if you’re not hunting for them, you may be missing them.
Understanding the adversary’s playbook
“You have to understand the adversary,” said Cristian Rodriguez, Field CTO of the Americas at CrowdStrike. “When we take an adversary-based approach, we understand what their techniques and objectives are.”
CrowdStrike categorizes cyber adversaries in three ways, he said.
One group consists of hacktivists, who are looking to make a political statement. They may, for example, vandalize the website of a government agency or company whose policies or actions they disagree with. Another group, ecriminals, are financially motivated and may deploy ransomware to achieve their monetary goals. “They’re noisy—they get in and get out fast,” Rodriguez said.
The third category consists of nation-state threat actors seeking intelligence or influence over events in specific target countries. They are prepared to infiltrate organizations and wait patiently, looking for chances to penetrate further before beginning to exfiltrate information or conduct other nefarious operations.
Hostile nation-states tend to not use malware or botnets for initial penetration. “Operational relay box (ORB) networks are more sophisticated and usually used by nation-state actors,” Rodriguez said. “There’s a dedicated infrastructure—infrastructure as a service—to anonymize traffic.”
Each nation-state group has different areas of expertise, he added. For example, China-nexus adversaries are skilled at exploiting zero-day vulnerabilities, which are previously unknown flaws in hardware, software or firmware. This gives them an advantage: Because these flaws aren’t known, they don’t yet have patches or fixes available, he explained. Russia-nexus adversaries, on the other hand, focus on developing proficiency in specific environments, such as Microsoft 365.
The Democratic People’s Republic of Korea (North Korea) doesn’t quite follow these patterns. While its exploits are nation-state-sponsored, they often have the goal of financial gain. The Hermit Kingdom is closed off from international commerce and finance; as a result, it needs hard currency. CrowdStrike data shows DPRK-nexus adversaries consistently target defense and aerospace entities in various countries, and they often seek to plant malicious insiders who could gain internal access to systems.
Changes in hostile activity demand a strategic shift
As evidenced by the use of insider threats, malicious activity is increasingly blending in with normal business operations. Adversaries are using legitimate tools and credentials to operate under the radar and evade detection. This means many of the cybersecurity measures organizations have invested in, such as signature-based malware detections, were built to prevent a decreasing proportion of the threats they face.
Organizations must also keep pace with adversaries’ accelerating speed. The average ecrime adversary breakout time—the time it takes an intruder to move from the initially compromised host to other places in the target environment—is quickly dropping. In 2024, the average breakout time observed was 48 minutes, CrowdStrike found, down from 62 minutes in 2023. And the fastest recorded time was just 51 seconds, meaning defenders may have less than a minute to detect and respond before attackers establish deeper control.
Adversaries are learning what works. As discussed in the CrowdStrike 2025 Global Threat Report, this includes social engineering techniques. “We are seeing a push to social engineering, since humans are the weakest link,” Rodriguez said. “The shift to identity-based attacks, using valid credentials, is rising significantly. So as a hacker, I would either phish or socially engineer identities, or I would use a purchased identity.”
The increase in identity-based attacks is why CrowdStrike’s report includes statistics on the rise of access brokers, which are specialists who acquire access to organizations and sell it to other threat actors. Access broker activity surged in 2024, with advertised accesses increasing by nearly 50% over 2023. Valid account abuse was responsible for 35% of cloud-related incidents, reflecting attackers’ growing focus on identity compromise as a gateway to broader enterprise environments.
This includes the cloud, which is another growing attack vector. New and unattributed cloud intrusions increased 26% between 2023 and 2024, a sign more threat actors are seeking to target cloud environments. Adversaries often use valid accounts to access cloud environments—and from there, they may use cloud environment management tools for lateral movement and abuse cloud provider command line tools.
“Once they get cloud access, they’re living off the land, using the same tooling I use,” Rodriguez said.
Conclusion
In March, Secretary of Defense Pete Hegseth issued a memo directing DoD acquisition processes to “adopt the Software Acquisition Pathway (SWP) as the preferred pathway for all software development components of business and weapon system programs in the Department.”
“This encourages the acquisition organizations in DoD to use ‘Other Transactional Authorities’ to purchase COTS software,” Rodriguez said. “In other words, to treat software differently than tanks. They’re trying to get to a 90-day cycle. I think that could be a good way to get today’s cybersecurity technology in place.”
One way the DoD can increase speed is by using private industry for incident response, especially in lower-classification networks. This can accelerate remediation, bolster cybersecurity, save costs, allow for innovative ways to defend the DoD, and give current DoD incident response teams more time to focus on more sensitive networks and incidents. Partnering with industry for incident response is a necessary and common practice in the Fortune 100s and, in theory, would have positive outcomes for the department.
A true defense-in-depth approach goes beyond routine patching and software updates. It requires that all levels of cybersecurity defenses talk to each other, comprehensively and quickly.
This is why it’s critical to adopt a cybersecurity methodology that embraces defense in depth with the power of cloud software as a service (SaaS). It provides faster outcomes, protects against pervasive and persistent nation-state adversaries, helps with human capital cost and gaps, and provides a fixed predictable cost.
Today’s adversaries have adapted to bypass traditional security measures,” Rodriguez said. “They no longer trip alarms—instead, they blend in using legitimate credentials and tools. To detect them, defenders must understand the adversary’s tactics, techniques and motivations, and proactively search for behaviors that don’t belong. It’s about thinking like the adversary and using global intelligence to uncover what others miss.”
CrowdStrike’s recommendations for today’s threat environment:
- Secure the entire identity ecosystem.
- Eliminate cross-domain visibility gaps.
- Defend the cloud as core infrastructure.
- Prioritize vulnerabilities with an adversary-centric approach.
- Know your adversary and be prepared.
For more information, download the CrowdStrike 2025 Global Threat Report at crowdstrike.com





Comments