Wireless Common Vulnerabilities and Exposures Continue To Escalate
Wireless communication has become the backbone of modern connectivity, but its ubiquity brings an ever-growing set of vulnerabilities. The latest data highlights an alarming trend: The number of wireless-related common vulnerabilities and exposures (CVEs) continues to increase annually.
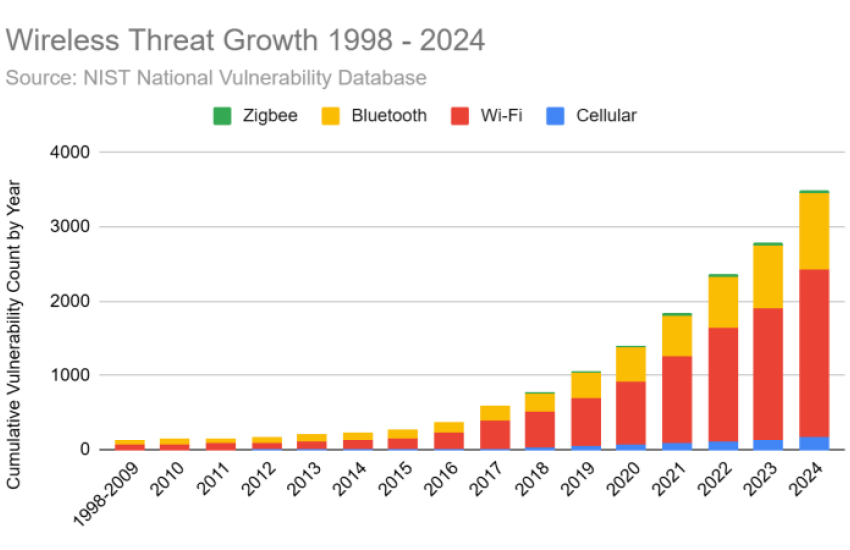
The cumulative count of wireless-related CVEs has skyrocketed since tracking began in 1998. A staggering 716 new wireless CVEs appeared in 2024 alone, accounting for 20% of all wireless-related CVEs recorded over the past 27 years. That is a one-fifth increase in known wireless vulnerabilities in just one year. (And so far, 2025 is also looking "up and to the right.")
This sharp increase underscores a key challenge in cybersecurity: What we know is only the tip of the iceberg. Published CVEs represent vulnerabilities researchers have identified, documented and disclosed to the public. However, they have yet to uncover many more vulnerabilities, some already known to malicious actors who exploit them before they are publicly acknowledged or patched.
Complexity Breeds Vulnerability
Why are we seeing this exponential growth in wireless vulnerabilities? One major factor is the increasing complexity of wireless protocols and systems. Wireless specifications become more intricate as technology evolves to support new use cases, such as advanced medical devices and personnel monitors. Each layer of added complexity introduces potential new attack vectors.
Consider the technologies driving this growth:
- Wi-Fi: The backbone of personal and organizational wireless connectivity continues to evolve, but each iteration brings new vulnerabilities.
- Bluetooth: Although Bluetooth is ubiquitous in consumer devices, its vulnerabilities have risen sharply as more critical applications leverage it.
- Cellular: As cellular networks expand and new protocols develop, the attack surface for cellular vulnerabilities grows alongside them.
- Zigbee and Other Internet of Things (IoT) Protocols: With IoT devices proliferating, attackers increasingly target protocols like Zigbee.
These technology interactions and the integration into increasingly complex ecosystems create a perfect storm for vulnerabilities to thrive.
For every published CVE, countless others may lurk beneath the surface, unknown to researchers but actively exploited by malicious actors. These zero-day vulnerabilities pose significant risks, particularly to organizations that rely on wireless communication for mission-critical operations. The stakes are higher than ever, from military-secure spaces to executive areas and data centers.
For additional details, see https://bastille.net/wireless-cves-explode-in-2024/.





Comments