Man and Machine Marry to Fight Cyber Attacks
The fully digital world has changed the strategies, tactics and procedures required to operate successfully in modern warfare. Highly skilled cyber analysts play an important role, but to achieve peak performance from both human and machine, automation within the network is needed. A new network approach—a single platform that is simple, automated, intelligent and secure—will better enable the U.S. Cyber Mission Force to operate within an enemy’s decision cycle and preserve U.S. supremacy across all five domains: land, sea, air, space and cyberspace.
Cyberspace is playing an increasing role in how wars will be waged and resolved in the 21st century. The modern military relies on it to conduct critical exercises—everything from tracking force movement to linking and gathering data across weapon systems and battlefield platforms, including aircraft, drones and robots. Cyberspace aids in the conversion of real-time data into decision-quality information used to help U.S. forces stay ahead of the enemy.
Although the domain has enhanced the military’s mission capability, it has created a complex national security environment with attacks so frequent that experts are looking at how both human and machine can work together to secure Defense Department networks, systems and information. At stake is the military’s ability to maintain the decision speed and operational agility required to sustain the strength of U.S. armed forces.
As the department builds toward full operational capability of its Cyber Mission Force, it should evaluate how it leverages human and machine. The Mission Force comprises about 5,000 individuals across 133 teams and is expected to grow to 6,200 people by 2018. With more than 30 million known malicious attempts to breach systems in a 10-month period from 2014-15, Defense Department networks will need more than human capital to keep up with the sheer volume, speed and intensity of sustained attacks. Because triumph in battle is increasingly about making decisions faster than an opponent, an effective cyber strategy should strike a balance between skilled cyber experts and tools and automation that provide speed and accuracy.
Time is of the essence, and the difference between human and machine reaction times can be significant. A person’s reaction time is a physical response to stimuli and a crucial component for dodging any kind of bullet—physical or cyber. The average bullet travels 2,500 feet per second, or around 1,700 mph. If a person needed 0.20 seconds—twice that of the fastest Olympic sprinters—to react to the sound of a gun going off, then that person would have to be at least 500 feet away to successfully dodge a bullet. The problem: Sound travels at 1,126 feet per second, or 768 mph. That means the bullet would hit the person before he or she even heard the gun fire. In sharp contrast to a human warfighter, a learning or automated machine will react to a cyber attack in milliseconds. Machines, then, can respond effectively as an attack is unfolding.
Automated machines can assess circumstances based on specific policies and scenarios and immediately execute commands to thwart an attack and maintain combatant commands’ battlefield effectiveness.
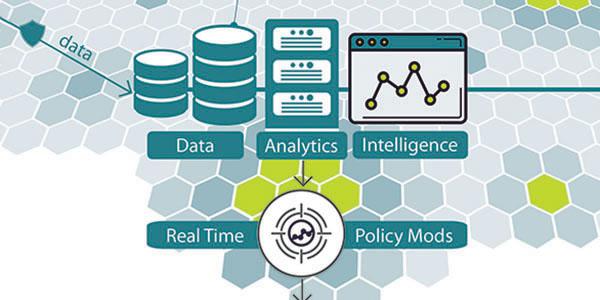
In building and operating the network as a warfighting platform, the Defense Department could consider a Digital Network Architecture (DNA), an approach used by Cisco, to facilitate faster, more flexible network services that support digitized mission processes. This architecture is grounded in a network infrastructure that is fully programmable and open to third-party innovation and seamlessly integrates the cloud as an infrastructure component. Its controller aids simple, automated and programmatic deployment of network services. It brings the notion of user- and application-aware policies into the foreground of network operations. Agencies today need a network capable of providing continuous feedback to simplify and optimize operations as well as to support an automated millisecond response to cyber attacks.
Embracing this type of architecture can lay the foundation for a fundamental transformation of cyberspace. First, closed and hardware-centered models give way to open, programmable and software-centered ones. Second, manual, repetitive command line interface-driven management is largely superseded by policy-based automation. Third, network-embedded, context-based security that reaches from the combat cloud to the battlefield edge supplants perimeter-based, reactive security. And last, information technology-centered analytics morph into mission-focused cybersecurity analytics. With this architecture, operators can specify policy for cyber infrastructure, and automation allows the technology to become far more nimble and respond to mission conditions more quickly and intelligently.
Defense agencies should evaluate a network architecture at its core on whether it can deliver what they need today and whether it is flexible enough to adapt for the future. A modern, digital-ready solution has four components.
The first one is virtualization. Information technology infrastructure virtualization through the decoupling of hardware from software gives the Defense Department the capability to run services on any platform and to deploy mission applications rapidly over the network to the battlefield edge.
The second component is automation. Scalable orchestration and controller capabilities simplify the information technology infrastructure through abstraction and automation to provide a platform for consistent policy enforcement. This speeds up application and service rollouts and reduces the cyber attack response time to milliseconds. It also builds trust and confidence in Defense Department systems, and cyber warriors gain time to focus on their mission instead of information technology operations.
The third is analytics. With the right architecture, the network can reveal patterns in the noise, provide rich contextual insights to users, applications, Internet of Things (IoT) devices and sensors, and identify threats for rapid decision making.
The digital network can amass real-time data across linked platforms, weapon system components and behavioral analysis algorithms. It can collect telemetry from every packet. A digitally enabled network can analyze millions of events and provide actionable insights from billions of records in seconds. It can retain data over the long term without loss of detail. From the F-35 to ground vehicles to the edge of the conflict, the network helps turn data into decisions. These analytics and information-sharing tools are critical to intelligence, surveillance and reconnaissance capability.
The fourth and final component of a modern network architecture is cloud services, which enable fast service adoption with on-demand scale and support for a broad array of mission applications. Extending cloud services to warfighters will require a mobile, survivable, secure combat cloud capable of operating in degraded conditions and while under cyber attack. A combat cloud is a software platform that provides a common framework to manage operational data and applications while analyzing the data by using automated mathematical algorithms and analytics.
Each of these components combines to create a new blueprint for modern digital warfare. The network extends to embrace and link all Defense Department systems, including enterprise, tactical, data center, cloud and IoT infrastructures. The result is a streamlined decision-making platform that maintains connectivity, scalability and performance characteristics that mission-critical systems need. This architecture would deliver network services to enable ubiquitous connectivity; security services to protect data and user integrity; and digital services to optimize mission applications.
No longer can manpower and policy be the key elements in configuring networks and securing critical assets with command-line tools, scripting interfaces and network management systems. With speed and precision being the battle cries of the day, this approach falls well short of what cyber warriors need to stay ahead of adversaries. Traditional legacy network operations and maintenance practices that do not incorporate automation compound three major challenges that lead to about 80 percent of all cyber incidents in the Defense Department. These factors include poor user habits, poor implementation of network architectures and poor network and data management practices. Legacy networks are extremely costly to operate, require highly skilled people to manage and do not enable innovation, which is necessary to bring greater mission efficiency and operational savings.
Automation has not made people obsolete. The full potential of innovative and leading-edge technologies is realized only when they are put in the hands of capable operators. Bringing skilled operators together with automated network platforms to build a full-blown warfighting platform is critical.
Carl De Groote is senior director, U.S. Department of Defense, Cisco. The views expressed are his own.





Comment
This is interesting
The fully digital world is THE EVOLUTION .
Informative !
Informative !
Comments