A Crucial First Look at the Nation’s Cyber Attack Surfaces
Never before has there been a holistic view of the nation’s cyber attack surface, by county. Thanks to researchers at the University of Maryland, counties can assess how vulnerable their IP addresses, public-facing nodes and databases are, and compare that to other counties, says Ido Sivan-Sevilla, an assistant professor at the university’s College of Information.
Sivan-Sevilla, with fellow University of Maryland researchers Mark McDermott, and Charles Harry, a former National Security Agency cyber expert, published their early findings in the U.K.’s Journal of Cybersecurity (Tyae-032) in January 2025, entitled, “Measuring the size and severity of the integrated cyber attack surface across US county governments.”
“We realized that there is a neglected aspect when it comes to government cybersecurity that is happening in counties, meaning that we do not have full visibility on what is going on in terms of the levels of cyber resilience of those counties,” Sivan-Sevilla explained. “The counties have an online presence and we wanted to know how it is being managed from security point of view, because hackers are constantly looking for the weakest link where they can penetrate a network with a successful initial attack vector, and then go from there.”
County governments provide their regions and citizens with online services, from school boards, wastewater infrastructure, housing, construction permitting and more. At the same time, they usually struggle with limited budgets for deploying security to their infrastructure.
“Given their impact on society, documented gaps in county government cybersecurity are alarming,” the researchers stated. “County governments collect and process sensitive information about U.S. citizens, manage regional arrangements for emergency and police response, facilitate elections, supply water to citizens, operate local school districts, and are responsible for developing local economies. Even though those local sectors are not traditionally considered ‘critical infrastructures,’ the consequences of poor cybersecurity at the local level can be disastrous.”
To gain a view of the cyber-attack surface, University of Maryland researchers collected data on 42,735 internet-facing devices across 3,095 county governments, representing 98% of all U.S. counties.
In their data examination, they had to be careful not to identify the information in such a way that would reveal the exact vulnerabilities for cyber marauders.
“We did not want to poke, nudge or even accidentally make counties more vulnerable in their online presence, so we used passive reconnaissance tools to understand how the attack surface looks,” he explained.
The researchers relied on open-source intelligence (OSINT) tools, including Shodan and Censys, “to stitch everything together, to be able to constantly monitor what is going on,” Sivan-Sevilla noted. They constructed a secure Python application to input the scanned information, including identifying Common Vulnerabilities and Exposures (CVEs), to estimate the relative size and severity of the cyber-attack surface based on county web-based platforms.
“Our findings reveal how nuanced the regional attack surface of county government infrastructures is,” the researchers noted in the published study. “We show that exposed county services follow a Pareto (power law) distribution, and maintain a positive correlation between the amount of services exposed and county population, and a positive correlation between the number of IP addresses publicly accessible in a county and the number of open ports and services available for potential exploitation.”
The researchers identified four of the most common types of cyber-weaknesses for which the counties were at most risk in a cyber attack, including:
- DDoS [distributed denial of service]-based threats (given DNS misconfigurations).
- Illicit access to critical government databases (by potentially exploiting publicly accessible Microsoft Structured Query Language (SQL), MySQL or PostgreSQL database management tools).
- Weak authorization practices for remote access, file management and network services using insecure Telnet, File Transfer Protocol, Remote Desktop Protocol and Secure Shell Protocol applications.
- Insecure file sharing, such as through Network Basic Input/Output System and Server Message Block protocols, which enable file sharing and printing in Microsoft Windows, the access point of the notorious WannaCry ransomware attack.
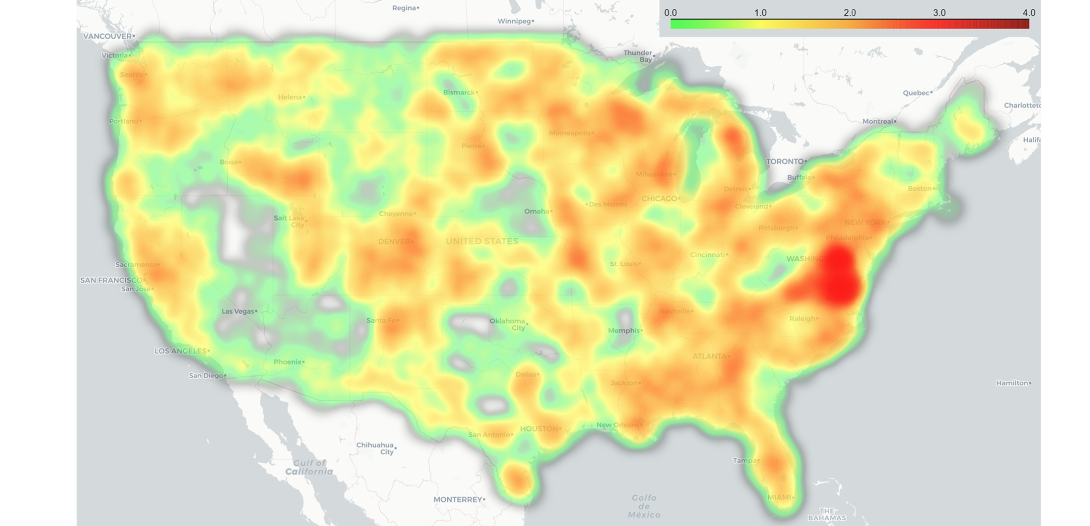
To capture the diversity of the attack surface, the University of Maryland researchers rated each county on a scale of zero to four based on the four possible critical attack vectors. They created a heat map (see below) that displays the most vulnerable areas of the United States.
They found that county cyber vulnerabilities, at scale, could cause serious damage to the nation.
And regionally, the eastern half of the country, where population centers are located, appears to be most diverse in the opportunities for exploitation by malicious actors. The state of Virginia—surprisingly given its technology company base—had a large number of digital access ports.
“When analyzing open and publicly available ports per county, and aggregating the data to the state Federal Emergency Management Agency region levels, we see that different regions are differently exposed,” the researchers’ study noted. “Twenty-seven states expose less than 1,000 ports each, with Delaware and Rhode Island on the lower-end, exposing less than 100 distinct open ports each. Twenty-three states expose more than 1,000 ports, with Virginia exposing more than 4,000 unique ports when assessing all of the IP infrastructure evaluated in its jurisdiction.”
In addition, the researchers found that it is not only the size of the potential attack surface, but also the quality of the exposed attack surfaces, meaning how fruitful certain vulnerabilities may be.
“As counties get more and more populated, they expose more and more services to their residents, so there are more opportunities to attack right,” Sivan-Sevilla said. “The diversity of the attack surface is higher for populated counties, so there is a clear correlation between population and diversity of the attack surface. But we also want to know, and this goes to the second type of measurement, of even if you expose so many services, even if you have those CVEs, how likely am I to use the CVEs as a hacker and really make an impact on your network? And that’s where the probability of exploitation and severity of exploitation kicks in.”
This aspect of quality comes from the conclusion that only about 3% to 5% of all CVEs found in software are actually being exploited.
“This is a very, very important point of reference, because counties do not have the resources to patch everything all the time. They have to focus. They have to prioritize. We’re trying to help them kind of prioritize and identify what is important, what is less important, and they should direct their resources to, and with those different quality measures of the attack surface.”

And while the potential damage is great, it does not necessarily mean counties will be attacked.
“It is important to note that exposure of a service in and of itself does not mean it can or will be attacked,” the study cautioned. “Attacks often require a service to be misconfigured or compromised through exposed credentials. Despite this limitation, mapping exposed services in the attack surface does highlight potential vectors of attack across the entirety of the integrated attack surface.”
The University of Maryland researchers are following up with a pilot project with local counties, to help them understand the external view of the attack surface that the researchers found and the next steps of action to add protections.
“And maybe at the end of the road, we can also create some kind of a ‘Race to the Top’ between counties, for counties to improve,” the professor stated. “And if we have full visibility on what is going on, enable policy makers at the state and at the federal level, at the CISA [Cybersecurity and Infrastructure Security Agency] level, to understand how to develop resources to help.”
The group is also presenting to both state and federal officials, including the state of Maryland, about how the governments can leverage the findings, in the short- and long-term.
“The impact of our study is also global,” Sivan-Sevilla continued. “The World Bank is very interested in what we are doing, because the World Bank is measuring cyber risk for developing countries just based on soft indicators, like ‘do you or do you not have a strategy for cybersecurity.’ At the international level, no one is using computational tools to actually get a holistic view of nations’ attack surfaces. So, for them, it is kind of a breakthrough way to measure cyber risk. And we are in conversations with them about making this usable for third-world countries as well.”
Additionally, the researchers are expanding their work to produce two more studies. One considers temporal trends of the attack surface—how counties do over time, adding digital services while making cyber improvements.
The other work involves an examination of patch management: “How well, in this case, counties patch problems,” Sivan-Sevilla shared. “We don’t know that at scale. We have findings from specific organizations, from specific sectors, and we know what drives patch management, and what types of things are getting fixed, perhaps quicker than others.”

We know what drives patch management, and what types of things are getting fixed, perhaps quicker than others.
The researchers would like to create an index, like those used in economics, for counties to understand their patch management response to problems.
And it is this type of assistance that makes the professor hopeful. “I never thought I would be an academic,” he shared. “I actually started in the Israeli Air Force, leading the cybersecurity team that protected the operational infrastructure of the Air Force. That was a great experience for me. I learned a ton in the Air Force. You get tons of responsibilities at a very young age, and you need to manage. That’s the best school I could ever hope for.”
After working on cybersecurity projects for the Israeli prime minister’s office, the professor won a Fulbright scholarship to study public policy at the master’s level, at the University of Minnesota, and then completed a doctorate in public policy at the Hebrew University of Jerusalem.
“I realized that I could really make a significant contribution in trying to bridge those two separated disciplines of computer science and public policy.”
For part of his doctorate, he conducted a study to measure the behavior of hackers, creating highly interactive ‘honeypot’ infrastructures to learn about hackers.
In addition, Sivan-Sevilla created the Technology Policy Hub at the University of Maryland, a confluence of public policy, cybersecurity, privacy rights, security compliance, assistance and information integrity.
“I established the Tech Policy Hub where we are using computational tools to understand tech policy implementation across different domains of cybersecurity, consumer privacy, information integrity and trustworthy machine learning.”
“Given my background and my own research agenda, it is about how can we actually be a bridge between how system requirement implementation and the policy regimes that protect them,” he shared. “This is kind of a classic use of computational tools to better understand how the risk looks over time and whether or not counties are responsive to the problems.”





Comments