Disruptive By Design: The Modernization Double-edged Sword: A Look at OT Cybersecurity in the Maritime Industry
Most people have encountered some form of operational technology (OT) without even realizing it. OT is hardware or software that monitors or controls how physical devices perform, such as cranes on ports or ship dynamic positioning. If compromised, OT systems can easily debilitate production and product access. For example, a recent OT vulnerability has been found in port cranes—if exploited, it could prevent cranes from moving shipping containers, or conversely, it could be used to throw containers around and cause mayhem. Recently, we’ve seen cyber attacks, both for information technology (IT) and OT, on the rise, and every industry should be aware of and mitigate their risks.
Maritime is one of the largest industries in the United States and operates through the maritime transportation system (MTS), which includes waterways, ports and land-side connections, moving people and goods to and from the water. With over 3,500 water terminals, it includes ships within the commercial, civilian government and military sectors. The MTS contains thousands of OT systems that control anything from port cranes to a ship’s engine or navigation system. Additionally, each port has different OT systems due to its particular purpose—a cargo port will have more OT systems supporting the movement of shipping containers, whereas a cruise port will support the movement of people.
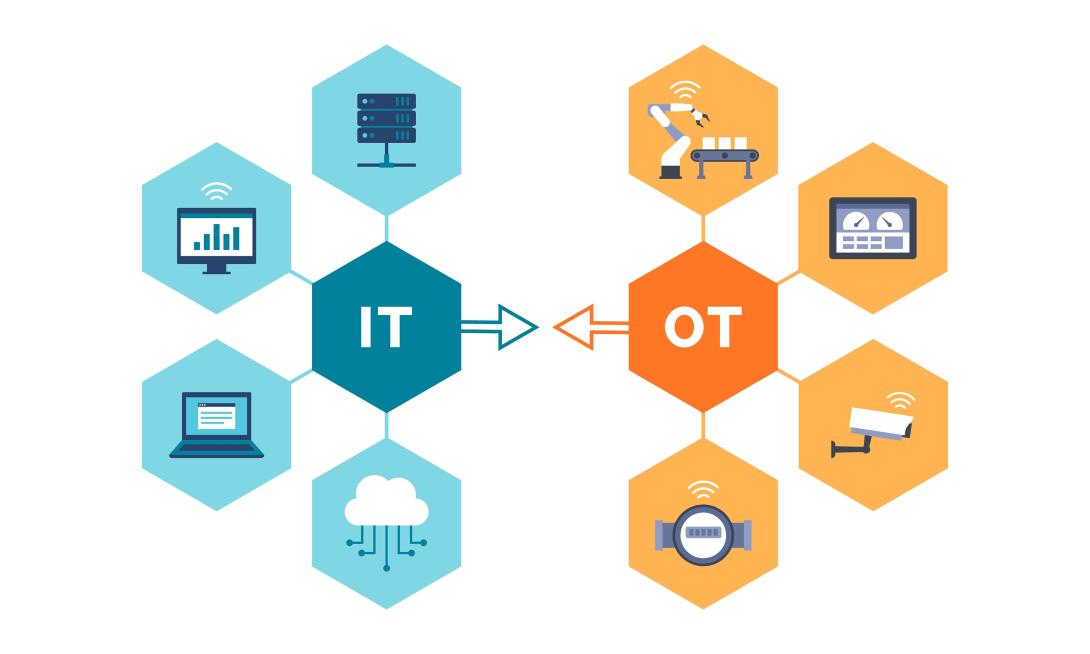
As new technologies are developed, they are often added as additional functionality on legacy OT systems built in the late 1990s or early 2000s, the beginning stages of the internet and connectivity. In recent years, these legacy OT systems have been connected to the internet to provide stakeholders with remote access to control the systems worldwide. This IT/OT convergence allows for a more globally connected workforce, but it also opens another avenue for cyber attacks.
The IT/OT convergence causes boundaries to blur between IT network functions and OT critical control functions, presenting a challenge for operators to understand fully how the systems interact with one another. In a worst-case scenario, this misunderstanding prevents operators from quickly restoring operations in the event of a cyber incident within the ship’s network. To identify vulnerabilities at the IT/OT convergence, OT cybersecurity specialists perform security assessments using enterprise IT tools and approaches. These assessments often cause more harm than good in OT environments as the assessments were created with IT systems in mind and OT systems interact with the network differently than their IT counterparts. Additionally, OT systems can contain hardware unable to withstand some types of assessments, which can cause a shutdown, particularly on legacy systems.
Modernization can be a double-edged sword; increased connectivity allows for immediate access control, real-time operations data and adjustments, but an adversary could use that same connectivity to debilitate MTS operations such as port functions or vessel movement.
OT systems often serve as the backbone for many processes in the maritime industry and other critical infrastructure sectors. While technology modernization creates an environment with increased collaboration, communication and connectivity, it usually doesn’t consider securing legacy systems. OT cybersecurity, as a practice, must find a balance between being innovative enough to keep up with ongoing threats while also maintaining tools and practices capable of communicating with legacy systems to secure their OT environment. Additionally, OT systems are inherently different from their IT counterparts; these differences must be considered when developing cyber policies rather than being asked to fit into existing enterprise IT risk management frameworks and approaches, thereby causing a “square peg in a round hole” situation.

Comments