Search Results for "" The Cyber Edge ""
Not finding what you’re looking for?
10 of 962 Results
An Insider’s Perspective: Taking Zero Trust From Strategy to Execution
Today’s technology makes zero trust a reality, but organizations still tinker with the intrinsic parts.
Image

Cyber Constructs for an Emerging World
Experts identify priorities for protecting assets in a continuously threatened digital world.
Image
The Price of Choosing Software Profitability Over Security
Expert sees cyber attacks getting worse long before any improvements.
Image

Tips for Zero Trust Strategy Implementation Leads
Cybersecurity experts provide valuable advice for those implementing zero trust in the federal government.
Image
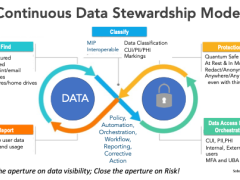
The Army Harnesses Software Acquisition Pathways
In fielding new solutions, the service is seeing initial success with a specific software acquisition effort.
Image

Addressing the Need for Secure Waveforms and Radio Equipment
The Army modernizes legacy waveforms and radios to retain overmatch against near-peer threats.
Image

Army Aims to Fully Push Electromagnetic Spectrum
Communications systems must fit the vehicle and the need.
Image

The Military Metaverse and the Future of Large-Scale Combat Operations
New approaches are needed to ensure victory in future operations.
Image

Shields Up: Improving Nationwide Safeguards
CISA’s effort offers a greater layer of protection against malicious cyber and critical infrastructure attacks.
Image
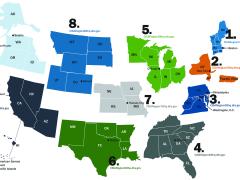
New Law Is an Opportunity To Grow Cyber Experience
Workforce program will allow federal employees to advance cyber skills through rotational positions.
Image
