Army Eliminates Enemies at Any Node
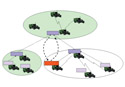 |
| Illustration of three network clusters in the Tactical Wireless Network Assurance Intrusion Detection System as it monitors, identifies, communicates with and responds to a malicious attack. During the system attack, the neighboring nodes of the accused identify the malicious node, gather information and pass that information to the clusterheads. The clusterheads determine a course of action and disseminate the verdict throughout the network. The computerized attack’s outcome is the elimination of all communications to the malicious node. |
Technology resembling the human immune system is enhancing security for ad hoc mobile wireless networks on the battlefield. It will automate operations; offer unique, enhanced protection to communications assets; and relieve troops from constant network-monitoring. The result is increased user trust in the network.
The U.S. Army’s Communications Electronics Research, Development and Engineering Center (CERDEC) recently created the Intrusion Detection System (IDS) as part of the Tactical Wireless Network Assurance (TWNA) Army Technology Objective. The IDS addresses a significant problem for battlefield network users. Namely, in a mobile, wireless network, anyone in range, including adversaries, can be connected. Connectivity gives enemies who capture a node the ability to attack the larger network. For example, a group of soldiers or combat vehicles could move through an area and stay connected with networked communications technology. If enemy combatants gain control of a vehicle or position and begin flooding the network with malicious traffic, the jamming attack could cause communications chaos and reintroduce the fog of war that the network-centric approach tries to dispel.
According to Christopher Fleming, a computer engineer at CERDEC who served as a technical engineer on the IDS project, the new system counters these types of routing attacks. The attacks are inherent in ad hoc mobile wireless networks because users are unaware of the specific identifications and locations of all other users and because the individuals connected to the networks are dynamic. Anonymity can be especially dangerous in the network-centric environment because many vital assets can be disrupted if persons with malicious intent gain access.
The IDS attacks enemy users with a method similar to the human immune system. When a virus enters a human body, the immune system detects the virus, disseminates alerts and eliminates the menace. The IDS counters network dangers in much the same way, pinpointing the node generating the attack and eliminating communications with it. Detecting and eliminating those threats in a mobile ad hoc network are more difficult than in a static network with stable infrastructure and access points.
By eradicating network threats, the IDS gives troops more confidence in their tools. “It’s important you maintain trust in your communications,” Fleming says. Military personnel gain no benefit from bringing radios into the field if links go down regularly. Just as individuals become frustrated and switch carriers when they have continual reception problems with their cellular telephones, troops become hesitant to trust networks that fail consistently and stop using them in operations. In such cases, warfighters may decide to send couriers to deliver critical messages instead of using unreliable radios. “It’s vital that these communications lines stay secure, or there won’t be any trust built into the network,” Fleming explains.
In addition to offering increased security and reliability to military networks, the IDS has other advantages for troops. One benefit is the autonomy of the technology. Once users complete the setup and initialization procedures, the system operates on its own except for maintenance or running an occasional script. The IDS runs in the background, enabling warfighters to focus on the larger mission rather than sit at a computer terminal monitoring the network. As personnel perform their duties, the IDS protects the network from information warfare attacks.
During the IDS development effort, CERDEC conducted two major experiments to examine the system’s effectiveness at combating network assaults. The first involved live testing with mobile wheeled devices. The second occurred in a laboratory setting with a realistic simulated testbed, which is a large network of computers that has tunable variables that mimic the battlefield environment. The variables include loss of throughput and outages in connectivity because of location and terrain.
Creating and employing the testbed proved to be some of the most difficult challenges researchers had to overcome. “The real difficulty was having the testbed and then really developing effective attacks that you can determine and eliminate,” Fleming shares. The testbed had to be reliable and consistent and to enable researchers to define a series of routing attacks. “To control chaos is not easy,” Fleming says.
The center collaborated with other agencies and private companies on the IDS, including the Army Research Laboratory, Telcordia and
Though CERDEC has completed its portion of work on the IDS, the organization continues to create technologies for a trustworthy communications environment comprising inherently vulnerable components through other programs and projects including TWNA. This Army Technology Objective develops and demonstrates network information assurance solutions for tactical mobile wireless networks, especially for Warfighter Information Network–Tactical and the Future Force. According to Stephen Lucas, CISSP chief engineer, Information Assurance Division, CERDEC, “Because the Army transformation of the Future Force will be highly dependent upon mobile, internetted C4ISR [command, control, communications, computer, intelligence, surveillance and reconnaissance] systems, it is critical that these systems be protected from compromise due to information warfare attacks.”
Lucas adds that technologies developed through TWNA “will prevent network-based attacks from compromising or diminishing the effectiveness of mobile computer systems and networks, help maintain warfighter trust [and] confidence in battlefield information and reduce system vulnerabilities.”
Capabilities developed through TWNA fit within the U.S. Defense Department’s vision of network-centric warfare. “The information infrastructure that supports this vision must be rapidly deployable, self-organizing, adaptive, self-contained, multilayered, survivable and interoperable with other military networks and the Global Information Grid,” Lucas states. “This new infrastructure is likely to be based upon the use of mobile ad hoc network technology—the mainstay of the Army’s Future Combat Systems program—that can dynamically form and reorganize communicating groups in the battlefield.” The infrastructure will incorporate a mixture of heterogeneous platforms such as unattended ground sensors, manned and unmanned ground vehicles, unmanned aerial vehicles and radios.
Web Resources
CERDEC: www.cerdec.army.mil
Future Combat Systems: www.army.mil/fcs




Comments