Military Leverage of Dedicated IoT Solutions
Internet of Things technologies, known IoT, have changed the operational paradigm of the defense industry, with military IoT applications and devices improving mission capabilities across a wide variety of mission domain areas.
Naturally, the U.S. military has more applications for so-called dedicated IoT solutions—where the IoT system drives the primary mission—as opposed to activities driven by ”everyday” IoT-connected devices, such as “smart” or Internet-connected doorbells, vacuum cleaners or refrigerators.
Dedicated IoT solutions for the U.S. Department of Defense (DoD) need to be ruggedized and in a small-form factor. And because commercial IoT solutions have security as an afterthought, military IoT solutions must have security as an integral part of the overall capability, especially given the increasing mission reliance on IoT technologies.
IoT Components
A typical dedicated IoT solution consists of a set of tactical-edge devices and sensors (edge devices), a data transport solution (an internet protocol (IP) based network) and a set of “central location” compute, storage and software. The edge devices collect data and transmit it over the IP-based network to the central location, where data is aggregated, correlated and processed into actionable events.
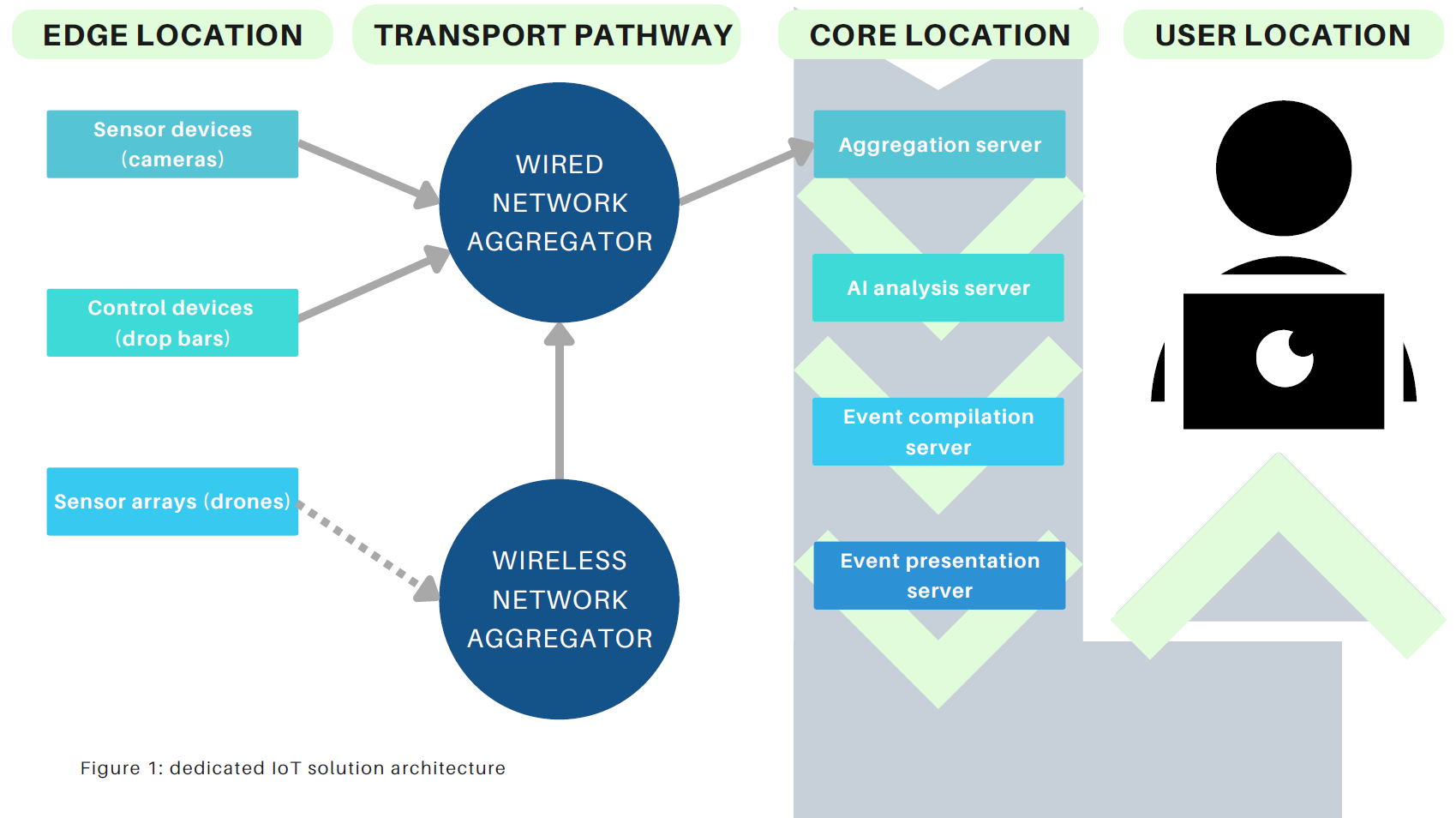
Edge devices generate large volumes of differing types of data: images, motion, heat, radiation. This information is aggregated and transmitted to a central location. After transmission, that data must be correlated and rapidly digested into an actionable event or decision. The data provides a more complete situational awareness of what is occurring at an edge location and gives operations sufficient information to initiate a viable response.
In addition to edge-sensing devices, some IoT solutions include edge-controlling devices that can actively control activity at the edge location, such as raising a drop bar at a security checkpoint. In more complex dedicated IoT solutions, some processing is done at the edge device location (edge computing). The most advanced IoT solutions use artificial intelligence (AI) to automate tactical responses then present those actions to humans who then formulate a strategic response.
Typical IoT Use Cases
Military IoT systems provide the ability for the physical world to be digitally monitored or controlled from remote locations. While most IoT systems control the physical world, IoT can also be applied to monitoring a virtual IT enterprise infrastructure, with remote monitoring and partially controlling all devices on a network.
In addition, military dedicated IoT solutions could broaden surveillance abilities. Recent advances in IoT technology—the integration of more capable edge sensors, faster networks and more powerful central location compute—have shifted solutions from larger-scale “whole-base” surveillance solutions to mobile “battlefield” surveillance—drones.
Military systems are often based on commercial technologies with IoT solutions that enhance battlefield wearables, infrared systems and military-grade command, control, communications, computers, intelligence, surveillance and reconnaissance systems and infrastructure.
Moreover, the military IoT market could be lucrative for industry. Based on the value of civilian IoT solutions that have military applications, estimates put the potential IoT military market at around $439 billion (in 2019 dollars), with an 11% annual growth rate.
Current use cases of IoT in the federal government and the DoD include:
-
Smart bases: The military uses commercial smart city and office automation IoT solutions to improve operational efficiency of military bases.
-
Real-time asset and fleet management: The military uses commercial fleet and asset management solutions for equipment and vehicles. Commercial IoT solutions are used to track asset/vehicle location, operating status and planned use.
-
Soldier health care: The military uses commercial IoT solutions to deliver health care to military soldiers in the same way as commercial health care providers.
-
Augmented reality/remote training: These aid in remotely maintaining complex military communications and battlefield equipment.
-
Gathering battlefield situational awareness/management: Location monitoring for equipment and soldiers, sensors for ground monitoring, equipment operability monitoring, soldier health and munitions monitoring, etc.
-
Target recognition and autonomous reconnaissance: Attached to smart bombs, sensors identify targets and guide ordinance to the desired target.
-
Identifying the enemy: Remote sensing equipment detects location, motion, infrared signatures, image recognition, etc., of potential enemy targets.
-
U.S. Department of Energy radiation safety management: Detect illicit movement of nuclear material globally.
Networking Considerations of IoT Solutions
To connect IoT edge-sensing devices, edge-control devices, multimodal networking technologies, compute and storage technologies, advanced AI and machine learning technologies, and emerging security technologies, a thoughtful network design is needed.
Historically, IoT networking technology solutions have been over wired IP networks. Many edge devices do not support IP networking, so network converters are required (e.g., to bring all devices on a single network platform). More recently, many sensing devices are wireless enabled, and some are cellular enabled. To accommodate this change, IoT systems now move this data to aggregation points where data is combined and shifted from wireless to wired transmission.
More complex network design (e.g., data segmentation) may be needed to ensure required enterprise data throughput can be maintained. IoT compute technologies consist of server hardware, physical storage and server software. Servers are smaller, but more servers are required as greater demand exists for aggregation, security, more complex human interface, more complex mission support and AI-based automated response.
Securing IoT Solutions
In military applications, IoT solutions can be a critical part of accomplishing a mission, so security is paramount. As shown in Figure 2, securing IoT solutions is performed at many levels: protection of devices that source data (i.e., protecting tampering of edge devices); protection of data in flight (i.e., protecting data along the entire path to the central location); and protecting the data at the central location (i.e., encrypting data at rest, access control, monitoring overall network performance).
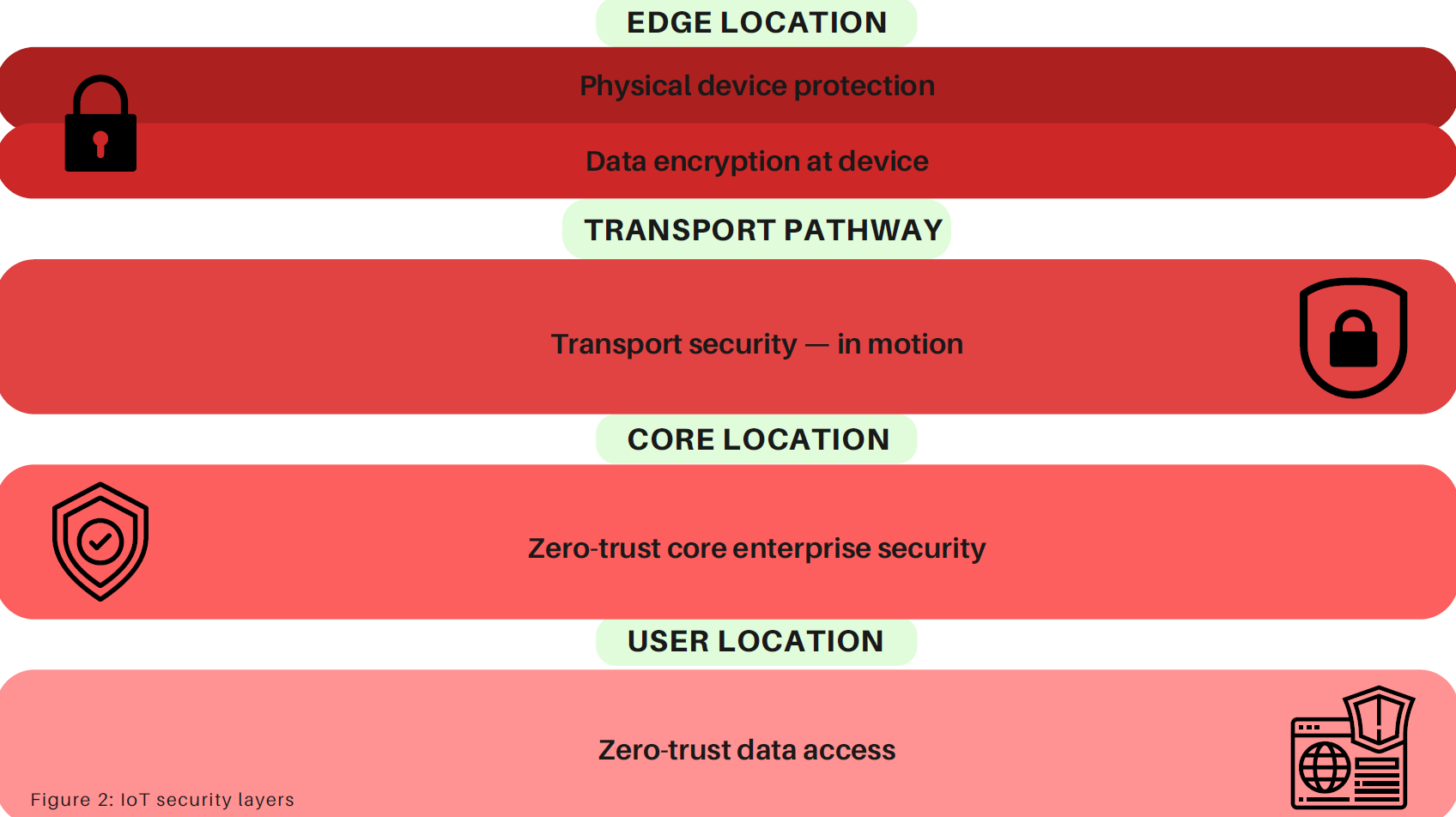
In securing these solutions, IoT system security designers must consider that IoT solutions operate in both core locations (e.g., a controlled environment) and at edge locations (e.g., an uncontrolled environment). Primary vulnerabilities of IoT solution components are compromised of core location components, compromise of the IP network, compromise of monitoring and/or manipulation of sensor data and compromise of edge devices themselves.
IoT systems can exist in a closed loop system or in a cloud-based hybrid environment. With hybrid solutions, network performance is more susceptible to external factors, and all security issues with a cloud solution have to be added to IoT security described above. With highly sensitive IoT solutions, IoT component supply chain must be more carefully considered to include examination of non-U.S. sensors.
When trying to choose or build an IoT solution, engineers need a good understanding of the host organization’s security and data sensitivity needs. It is critical to address data protection, physical and virtual protection of edge devices, and protection of the central information technology processing infrastructure.
Properly managing IoT cybersecurity must begin prior to mission operations. This involves understanding the integrity of end user device manufacturing. And for the DoD, it is about protecting the entire supply chain so enemies cannot inject corrupt components into critical operational systems.
This article, prepared in conjunction with AFCEA’s Technology Committee, is the first of four articles about Internet of Things (IoT) systems and solutions that are operating on fixed or mobile platforms. The second article will focus on advancing IoT data security. The third article will describe real-world situations where IoT is integral to mission delivery. The final article will focus on how emerging technology will further expand use of IoT technology.

Bryan Ward is a member of AFCEA International’s Technology Committee. He serves as enterprise architect with A3 Consulting LLC, a Baltimore-based 8A IT company.




Comments