A Top-Secret Smartphone Could Become Reality
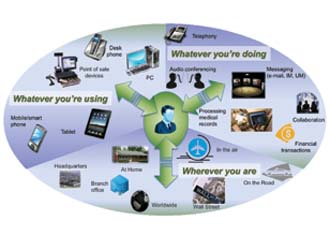 |
With the secure mobile communications initiative, users will be able to stay reliably connected to receive the most important data. |
Mobile technologies are advancing at a blistering pace, and the old way of communicating is being relegated to the history books. The question many government customers are asking right now is, “When do we get these new mobile platforms?” The answer might be surprising.
The future of secure communications lies in the ability to be reached reliably anytime, anywhere, regardless of the classification level. While solutions currently exist—such as the Secure Mobile Environment Portable Electronic Device (SMEPED)—the National Security Agency (NSA) realizes that the infrastructure required to support the program is near the end of its life. In addition, SMEPED platforms already have been overtaken by newer, more capable technology. Rapidly evolving systems have necessitated a move away from government off-the-shelf (GOTS) solutions to a more layered commercial solution. A secure commercial off-the-shelf (COTS) mobile solution must be developed to ensure uninterrupted service.
The NSA aims to produce a fully secured mobile communications architecture by leveraging only commercially available components and the collective expertise and knowledge of a newly formed mobility team.
A subset of the larger mobility group is a tiger team of 18 people in the Systems and Network Interdisciplinary Program (SNIP). This group has spent the last several months analyzing prospective components of commercial solutions—mobile voice over Internet protocol (VoIP) applications, mobile virtual private network (VPN) applications, VPN servers, communications servers and the mobile infrastructure itself—and evaluated how these parts provide the security needed to support classified communications. The team’s findings already have influenced the architecture of the first mobility pilot program and have set the groundwork for future mobile security.
Technology has reached the point where it is feasible to secure mobile communications. A review of the history of communications networks shows how they have evolved to be more secure.
Circuit-switched networks (CSN) have been around for many years. Communicating in this manner has worked reliably for decades. One reason is that each call was given a dedicated circuit, which meant a caller did not have to share the channel with any other callers. The CSN technology has provided the backbone of military communications for years and even has carried top-secret data.
In previous technology generations, mobile companies began building networks independently of one another. When cellphones started gaining wide use, there was a heterogeneous mix of equipment and protocols. Mobile customers began asking for ways to attain true mobility outside their local area. Thus, the Global System for Mobile Communications (GSM) standard was created.
Users of the original iPhone are familiar with Enhanced Data Rates for GSM Evolution (EDGE) networks, which are an enhanced version of the GSM network allowing for higher bandwidth. In the mid-1990s, another technology called cdmaOne, also known as code division multiple access (CDMA), was developed by Qualcomm and deployed ubiquitously in the United States in parallel to the GSM advances. Each of these technologies continues to advance, allowing higher throughput and more subscribers still relying predominantly on CSNs.
Prior generations of mobile phones could not handle the multiple levels of security needed for secure communications. Only recent mobile devices can keep up with security demands.
Mikhail Sosonkin, a member of the SNIP Endpoint team, states that, “In the past, technology was driven by corporations—an example would be a company issuing BlackBerry phones to employees—but today’s consumers have become the early adopters and want to use their devices everywhere they go, including the office.” As a result, not only is the NSA figuring out how to integrate this new mobile technology, but corporations are as well.
Packet-switched networks (PSNs), the successor of CSNs, are leading the way for next-generation telecommunications infrastructure. In addition to reduced costs for customers and companies, PSNs are ever-present and provide access to more devices.
When VoIP first was being used on the Internet, security was not built into the protocol, and connections could be tapped easily. However, in recent years, VoIP has made huge strides in securing data—not only the voice transmission of a phone call, but also the signaling traffic used to establish a connection between two endpoint devices. Typically, when a VoIP phone call is made, two communication channels exist. One is the control channel that establishes the connections. The second channel is where all the data—video or voice—traverses. For holistic security, both channels need to be protected. VoIP is now at a point where that is possible with Datagram Transport Layer Security (DTLS) and Secure Real-time Transport Protocol (SRTP).
When the SRTP was developed, it solved the problem of securing the audio and video streams between two parties. Nevertheless, one major flaw still existed. The vulnerability was that the keys used to secure the stream were sent unencrypted. To address this problem, the Internet Engineering Task Force (IETF) decided to use the DTLS in conjunction with the SRTP, and the DTLS-SRTP was created, which provides end-to-end security for the entire communications session. This provides one complete layer of security.
A VPN creates a secure, encrypted tunnel for digital traffic. This is a great solution for protecting data in transit. The VPN either can be hardware, software or a combination of both. For the recent past, RSA, a public-key cryptographic algorithm created in 1978, has ruled the world of VPN encryption. However, as with most algorithms, attacks have been developed and new algorithms are needed.
The NSA has been pushing Suite B, a new direction in cryptography. Suite B has a list of components and algorithms, but the most advanced algorithms surround elliptic curve cryptography (ECC). Adding to the allure of the stronger encryption algorithms is the shorter key space. A shorter key means less processing power is needed—good for mobile devices. A 384-bit ECC key is approximately equivalent to 7,000 bits of an RSA key. Software companies have taken note of the NSA’s push for Suite B and have written or are writing software that complies with Suite B specifications. The significance of this new development is that cryptography is a major component for securing mobile communications.
One category of products that inherently is tied to cryptography is the VPN. Its manufacturers also have started to integrate Suite B into their products. This provides an additional layer of protection. If a second VPN or Internet protocol security (IPSec) is added, three independent layers of security can be achieved.
There are definite advantages to using GOTS products, which reside mainly in controlling the entire production process. On some products, that type of control is needed. However, it does not scale well and is very expensive. With technology changing as rapidly as it has been, the GOTS solutions cannot keep pace, so COTS products are used.
The acquisition process of GOTS products typically is longer than that of COTS solutions, so there can be a time savings. Another advantage of COTS is the cost savings of the mass manufacturing of products. COTS products generally are installed easily and are interoperable with other equipment, which can save a tremendous amount of time and money.
Back when cellular companies did not interoperate, they had to invest large sums of money either into upgrading or retrofitting equipment to be able to talk with other carriers. The organizations learned a lesson from this, and now interoperability is taken into account during the design phase.
Hardware is now mature enough for a secure mobile solution. The next step is evaluating the best combination of components to achieve a secure, reliable communications solution. With all of the different parts of the project multiplied by all of the products in the marketplace, the number of permutations is high.
Troy Lange, cryptographic products engineering chief, says that, “Securing COTS mobile products is a daunting task.” He also notes that his focus is on mobile access to national security systems, which is exceedingly more complex than simply accessing the public Internet. To make this huge project more manageable, the SNIP team broke up into three focus areas: Endpoint, Ether and Enterprise.
The Endpoint team is looking at Apple’s iPhone devices, several phones supporting the Android operating system and laptops with the capability to connect to cellular networks. In addition, the team also is looking at several VoIP applications that support the required cryptography. Rounding out the Endpoint team is a focus on finding an appropriate VPN solution such as Cisco’s ASA device, OpenVPN or Strong Swan. The Enterprise team has been working on back-end VPN servers and VoIP servers such as Kamailio, SIP Witch and Asterisk.
One of the reasons that this project is such a challenge, in addition to its scope, is the different mindset of the security practitioners versus manufacturers, which are building products for reliability and ease of access. One example that was repeated by various project members was split tunneling.
Split tunneling occurs when a networked device is connected to a VPN and the public Internet at the same time. Most marketing material lists split tunneling as a feature because it can speed up the users’ experience when accessing resources that are not on the VPN.
However, as Rich Capone, the head of the Endpoint team, explains, “Split tunneling allows communications channels to be created outside the VPN and without user knowledge. The very nature of a VPN is to protect the data, but split tunneling renders obsolete that specific measure of control. From an attacker’s perspective, split tunneling also opens a door from the public Internet to the internals of a private network.” Security could be compromised if the phone were connected to some classified network while allowing split tunneling.
The Ether team has built a full-scale wireless network and is performing vulnerability analysis on each component of the network. To make a simple phone call, messages may be passed to more than 50 devices just to figure out where the distant-end phone is located. Each device is receiving multiple messages.
Lastly, the Enterprise team will bring together all the different components into a centralized place where the management of the network can occur. The team is looking at several enterprise products such as Microsoft’s Lync and Cisco’s Unified Communications System.
The SNIP team presented its findings and recommendations for future work on June 24 at NSA headquarters, Fort Meade, Maryland. The work the team has done over the course of several months already has been paying off. Within the short term, a mobility pilot program will be deployed as a test case for the numerous requirements within the Defense Department.
Analyzing commercial products and identifying ways to use them securely takes time. So while not everyone is going to be issued a secret Internet protocol router network (SIPRNet)-enabled iPad by a specific date, the SNIP team is working aggressively toward secure architectures. Once that goal is achieved, cutting-edge mobile devices surely will be part of the toolset of government workers.
Capt. Steven Pugh, USAF, is the commander of the 315th Network Warfare Squadron, Detachment 2, Lackland Air Force Base, Texas.


Comments