Military SSDs Are MVPs of Data Storage
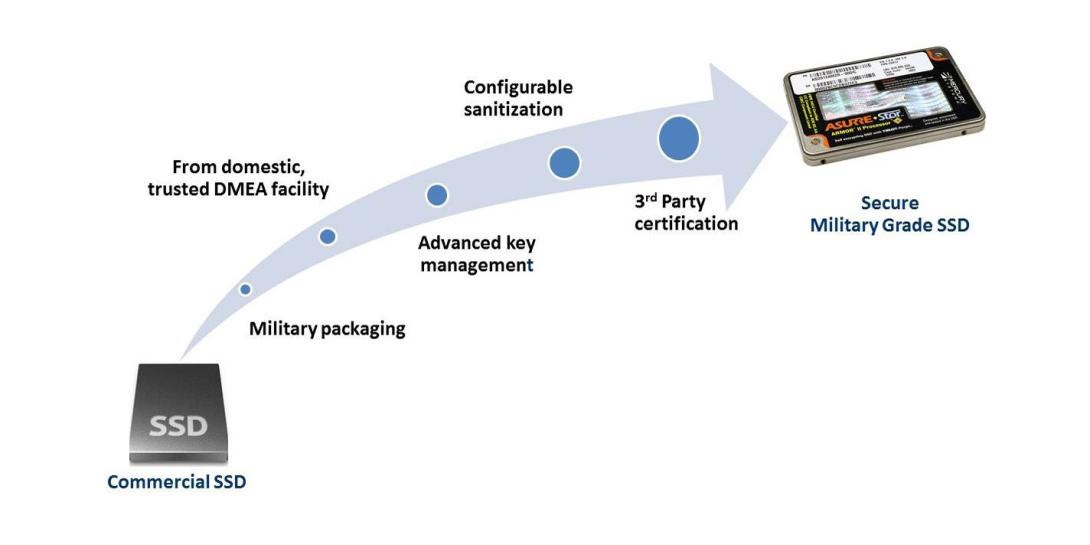
Solid-state drives store data using flash memory and are becoming common system-level components in military systems. Although they are inexpensive and readily available, commercial off-the-shelf versions often fail to meet military requirements: predictable performance under stressful operating conditions, robust ruggedization, long-term availability from an accredited supplier and trusted security. Drives designed for the commercial market do not provide the flexible security features needed in today’s modern military applications.
A military-grade solid-state drive, or SSD, incorporates security from the start, unlike a mass-market consumer product. It uses Advanced Encryption Standard (AES) with a 256-bit key encryption to protect data.
Because the security of stored data is directly linked to the strength of the data encryption key (DEK), how the DEK is generated and filled into the drive is an important design consideration for military systems. Commercial off-the-shelf (COTS) SSDs use DEKs that are generated internally and therefore allow no method to verify their randomness, or entropy. COTS SSDs with internally generated and stored DEKs must obscure or encrypt them. Verifying whether a COTS SSD is properly protecting the DEK is nearly impossible because the method used to secure the DEK is unknown. The DEK might even be stored in plain text.
An alternative is to generate the DEK externally using systems and algorithms that create highly random values and then fill the known key into the SSD—a process that strengthens security features. Because the host system fills the DEK at every power-on event, an unpowered SSD contains no discoverable key.
Military-grade SSDs better protect against hacking. While recovering even a plain text DEK stored somewhere inside a COTS SSD is likely beyond the abilities of the common hacker, it is not for a nation-state actor. Military-grade SSDs encrypt self-generated DEKs and accept passphrase lengths of up to 64 characters for enhanced security. Additionally, when properly integrated into defense equipment, these drives can detect physical tamper events or too many failed authentication attempts. In those cases, they respond by erasing the drive contents or performing a self-destruct operation. These features are rare to nonexistent in COTS SSDs but can greatly simplify the security implementation to protect highly sensitive data in modern defense systems.
Historically, such highly sensitive data has been safeguarded by Type 1 security solutions, devices certified by the National Security Agency (NSA) to encrypt classified information. The NSA’s Commercial Solutions for Classified (CSfC) program, which enables commercial products to be used in layered solutions that protect National Security System (NSS) data, mandates that two or more layers of CSfC-compliant components shield classified, secret and top secret information. CSfC program-validated devices provide system architects assurance that cryptographic algorithms in an SSD are certified and have passed rigorous testing by the National Institute of Standards and Technology (NIST) and the National Information Assurance Partnership (NIAP).
Although CSfC validation of an SSD is the pinnacle of third-party testing, other certifications can gauge suitability for mission-critical applications as well. At a minimum, the encryption algorithm should be validated as conforming to NIST’s AES algorithm, specified in the agency’s Federal Information Processing Standards (FIPS) Publication 197. The next certification level falls under NIST’s Cryptographic Module Validation Program (FIPS 140-2), which defines rigorous security requirements for cryptographic devices and has gained worldwide acceptance.
In the end, the use of COTS SSDs in defense applications comes down to trust. Are these storage devices rugged enough and secure enough to meet the challenges of military applications? If the answer is no, then military-grade SSDs clearly are better alternatives.
Bob Lazaravich is technical director at Mercury Systems. The views expressed are his own.





Comments