Search Results for "" The Cyber Edge ""
Not finding what you’re looking for?
10 of 962 Results
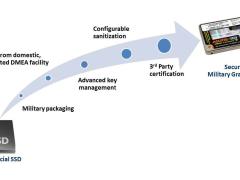
Military SSDs Are MVPs of Data Storage
These solid-state drives meet rising demand for security features in defense applications.
Image
How the Hashtag Is Changing Warfare
Armies of social media bots battle for hearts and minds online.
Image

The Quest for an Operational Cyber Edge
Soldiers do amazing things with cyber and electronic warfare technology prototypes.
Image

Army Accelerates Cyber, EW Integration
The service works to create a cultural shift and curb weaknesses as divides between disciplines disappear.
Image

More Than Just Your Regular Cyberthreats
Diverse issues dominate security intelligence agenda.
Image

Wanted: Top Technology, Talent for Federal Cyber
Filling gaps in capabilities and the work force will help the Defense Department better manage a deluge of threats.
Image

New Ransomware Attack Targets Europe, U.S. Bracing
Cyber experts in the United States are bracing for the effects of a massive cyber attack hitting Ukraine, primarily, and other European nations Tuesday.
Image

Tech Support Scams on the Rise
Does this call sound familiar?
Image
Getting Processors to Speak a Unified Cyber Tongue
A government-academia collaboration has researchers working to streamline different computer programming languages so that processors can speak in a single cyber tongue.
Image

Finding Cyber Talent in Unconventional Places
The struggle to hire cyber employees has increased with another ecosystem vying for the same shallow pool of qualified candidates.
Image
