Sponsored: Deception Technology to Outmaneuver and Reveal In-Network Threats
The ThreatDefend Platform provides accurate threat detection within user networks, data centers, clouds, and specialized attack surfaces.
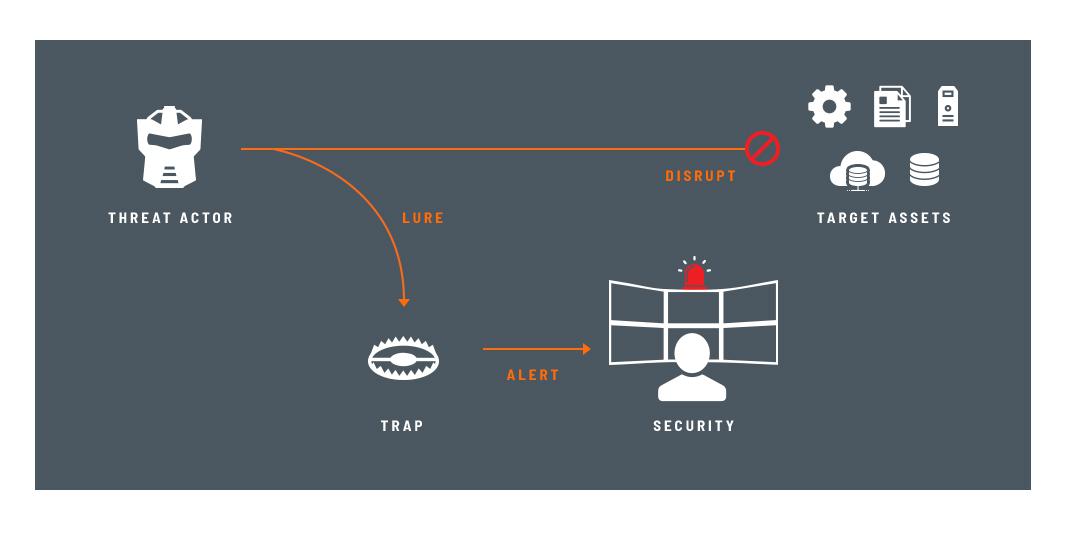
Deception changes the asymmetry against attackers with attractive traps and lures designed to deceive and detect attackers. Providing an active defense for early detection, forensics, and automated incident response to in-network threats is a must. The ThreatDefend™ Platform provides accurate threat detection within user networks, data centers, clouds, and specialized attack surfaces. The portfolio includes expansive network, endpoint, application, and data deceptions that misdirect and reveal attacks from all threat vectors. Advanced machine-learning makes deployment and operations simple to operate for organizations of all sizes. Attack analysis and forensics provide actionable alerts, and native integrations automate the blocking, quarantine, and threat hunting of attacks for accelerated incident response.
Attivo deception provides immediate value by providing “eyes inside the network” visibility and accurate detection alerting based upon decoy engagement or attempts to use deception credentials, most notably early in the attack cycle.
For years, attackers have successfully used deception tactics for breaching networks. They masquerade as legitimate employees, using stolen credentials and deceptive measures to infiltrate a network, all while remaining undetected for lengthy dwell times. Security teams are challenged in that they have to be successful 100% of the time, whereas an attacker only has to get lucky once. It’s now time to turn the tables on attackers and use deception against them. Outwitting an adversary is rarely accomplished without a balance of defensive and offensive measures
Deception brings the offense into the realm of cybersecurity with the ability to deceive and misdirect an attacker into revealing themselves. All, without false positive alert fatigue and the burden of operational overhead associated with traditional detection methods. Attivo, the leader in deception technology, stands apart in that the company uniquely empowers organizations with capabilities they cannot achieve with other security controls: the capacity to outmaneuver the attacker, force them to execute flawlessly, and ultimately derail their efforts using their beloved approach of deception. Learn more.



Comments